Threat Intelligence
Sophisticated Phishing Campaign Targets Corporate Credentials
June 26, 2019
Volexity has been tracking a series of phishing campaigns focused on harvesting Microsoft Office 365 account credentials. While many commodity phishing kits are available to purchase containing Office 365 themes, these specific campaigns have a level of sophistication not frequently seen in commodity attacks. Despite the level of sophistication, Volexity currently believes this activity to be tied to a criminal actor and not that of nation state or advanced persistent threat (APT) group. The activity observed by Volexity and described in this post matches what is known as a Business Email Compromise (BEC) attack. BEC attacks are designed to allow attackers to silently snoop on e-mail communications regarding financial transactions; a good example would be unpaid invoices. Once the attacker gains access to a target’s e-mail inbox, it is not uncommon to see them intercept and modify legitimate invoice documents (PDF/DOC), add their own bank account information, and send back to an unsuspecting target. Last year, the FBI released a public service announcement stating it believes BEC attacks have netted criminals upwards of 12 billion US dollars between 2016 – 2018.
Phishing E-mails
The image below shows an example of one of the recent phishing messages sent by this criminal actor.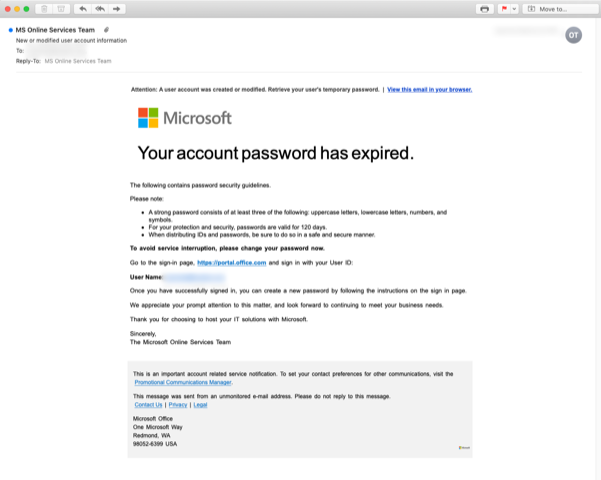
The campaign begins with an e-mail that claims to be a legitimate Microsoft notification regarding the recipient’s account password expiring. In the display field for the sender address, it is labeled as MS Online Services Team, and the sender domain used is closely structured to impersonate an actual Microsoft domain. The following senders were observed for this campaign. All four contained the same friendly/display name.
The attacker also employed a common tactic used by spammers in order to prevent automated keyword flagging and searching by inserting small white colored characters instead of spaces throughout the email. As shown below, the pattern for these white characters seems to repeat the pattern x o g d.
![]()
<p><strong>To<font style=”color:white; font-size:xx-small; font-family: ‘Courier New’, Courier, monospace;”>x</font>avoid<font style=”color:white; font-size:xx-small; font-family: ‘Courier New’, Courier, monospace;”>o</font>service<font style=”color:white; font-size:xx-small; font-family: ‘Courier New’, Courier, monospace;”>g</font>interruption,<font style=”color:white; font-size:xx-small; font-family: ‘Courier New’, Courier, monospace;”>d</font>please<font style=”color:white; font-size:xx-small; font-family: ‘Courier New’, Courier, monospace;”>x</font>change<font style=”color:white; font-size:xx-small; font-family: ‘Courier New’, Courier, monospace;”>o</font>your<font style=”color:white; font-size:xx-small; font-family: ‘Courier New’, Courier, monospace;”>g</font>password<font style=”color:white; font-size:xx-small; font-family: ‘Courier New’, Courier, monospace;”>d</font>now.<font style=”color:white; font-size:xx-small; font-family: ‘Courier New’, Courier, monospace;”>x</font></strong> </p>
The hyperlinked text in the e-mail for portal.office.com is actually a link leading to the malicious URL:
- portal.email.msmfaonline[.]com/?mfa=$Base64EncodedEmail
This URL will return a 302 response code, redirecting victims to the phishing page located here:
- hxxps://portal.microsftnonline[.]com/changePasswd/?mfa=$Base64EncodedEmail
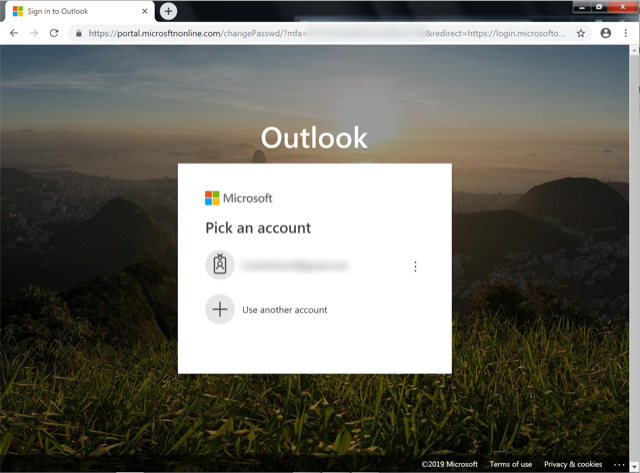
Office 365 Phishing Page
Example 1:
Example 2:
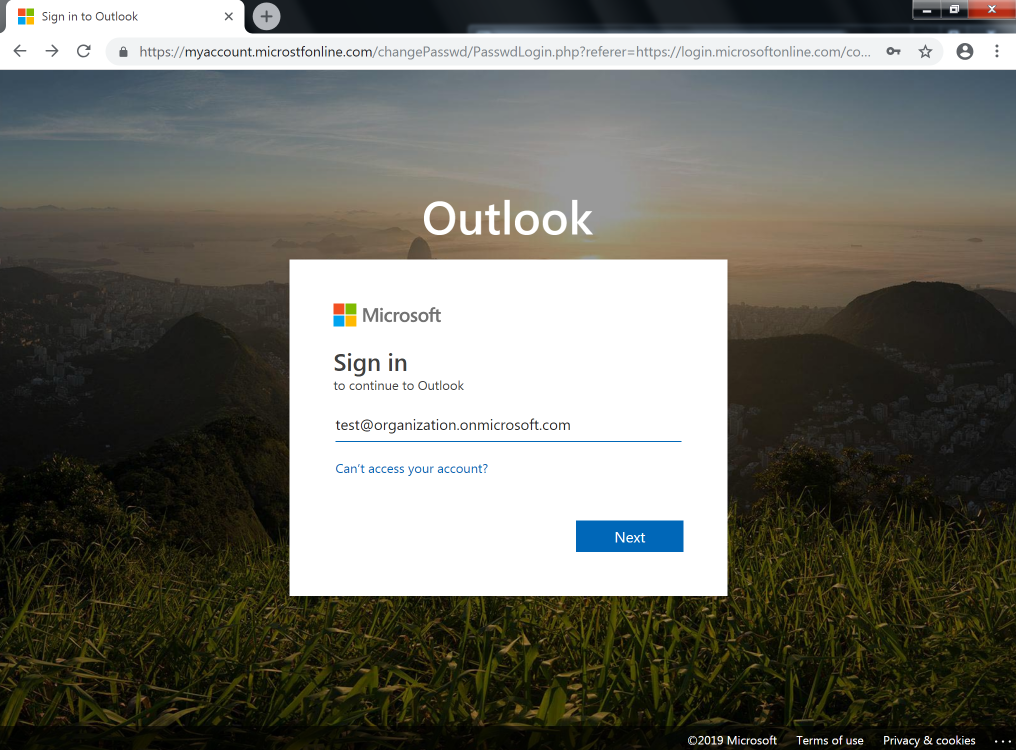
The phishing page is almost identical to the login portal available on microsoftonline.com (the legitimate login page); however, it does appear that the large Outlook text is not on the real page. Upon submitting credentials, the data will be transmitted via a POST request to a file named PasswdLogin.php on the same site. What is interesting is the attackers have a method to validate the credentials submitted. Through testing performed by Volexity, it was observed that immediately after submitting credentials, there were logon attempts for the account. Comparing timestamps for when data was submitted and the time referenced in logs generated by Office 365 confirms that the attackers have an automated process for credential validation. This is a feature not commonly observed in commodity phishing kits. Additionally, the attackers also seem to employ some tactic for blocking repetitive access to the phishing pages. After visiting the site and submitting information, subsequent requests will result in a 404 not found page being displayed.
Account Compromise
Although the phishing page itself contains some level of sophistication, once a compromise has occurred, minimal actions are performed by the attacker. In a compromise observed by Volexity, three inbox rules were created. This was identified through analysis of Office 365 logs where a New-InboxRule operation had taken place. These rules are described below.
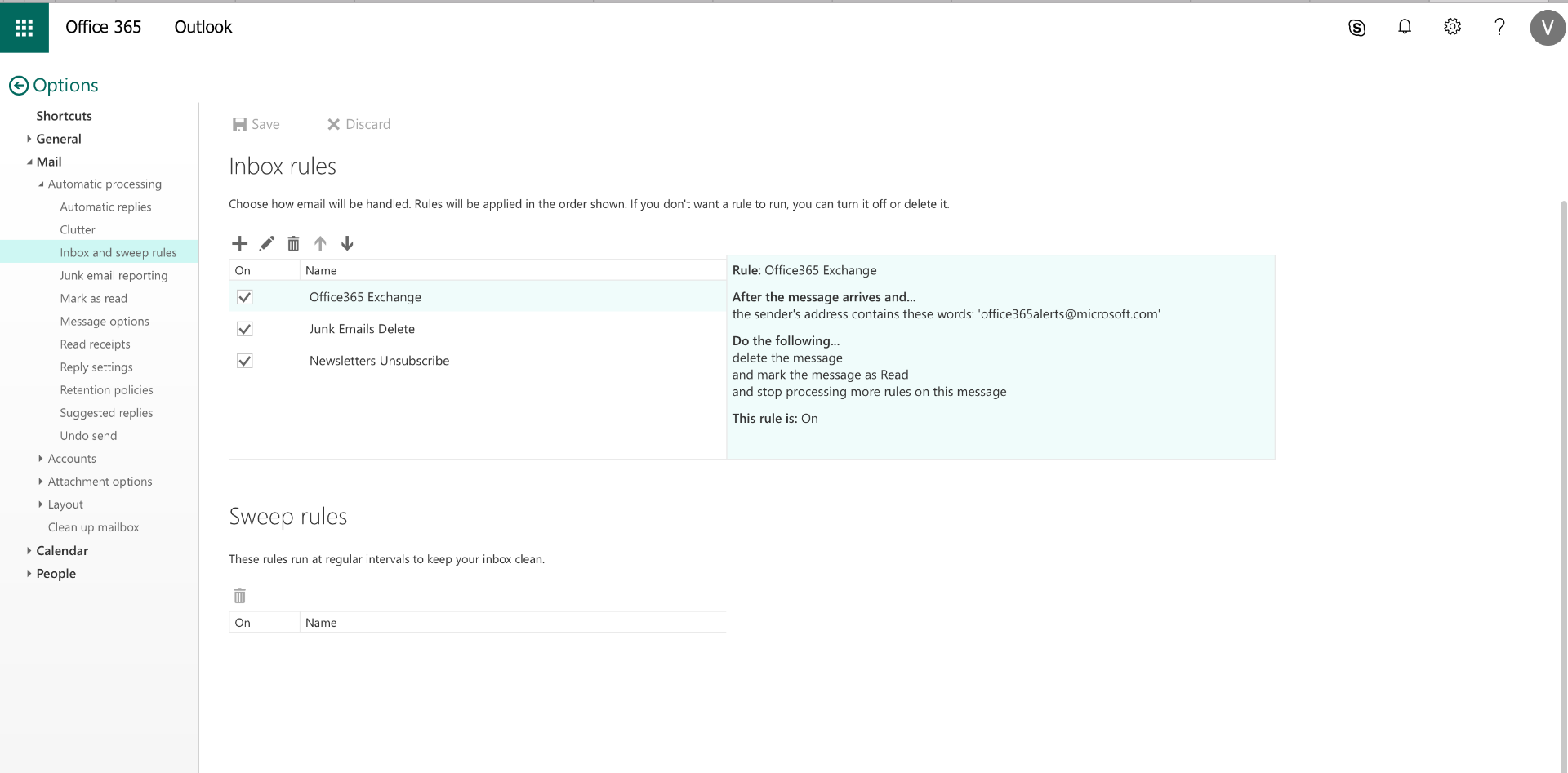
Rule Name: Office365 Exchange
Rule Function: Mark as read, delete, and ensure no additional rules are processed for any e-mails received from the address [email protected].
Rule Purpose: This rule ensures that any alerts Microsoft may send regarding unauthorized account access are not seen by the owner of the compromised account.
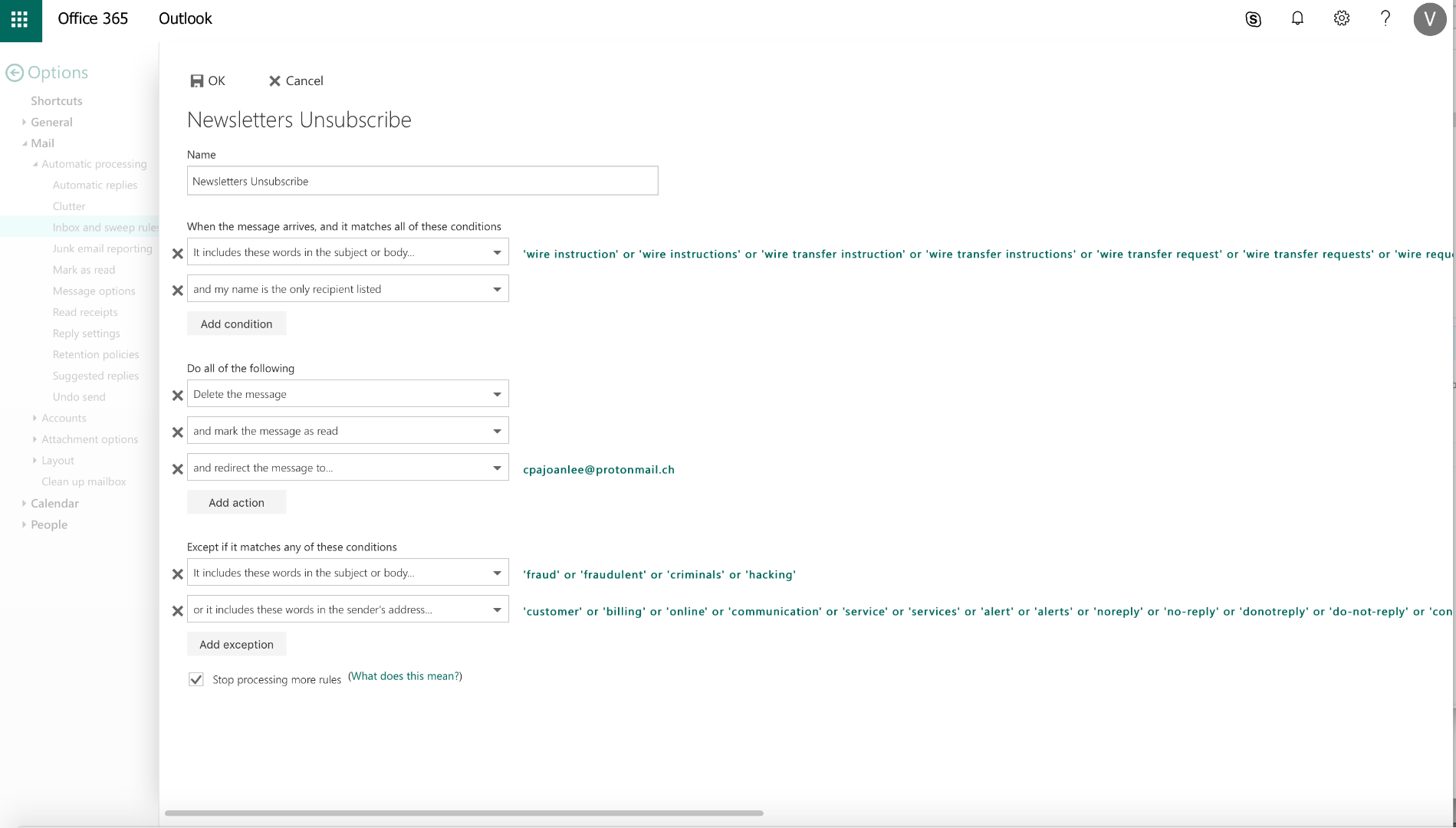
Rule Name: Newsletters Unsubscribe
Rule Function: Look for any e-mails containing banking information or wire transfer references, and forward the e-mail to [email protected], marking it as read and deleting it after. Additional keywords are looked for in the rule, which if met, will act as an exclusion and not forward to the protonmail address.
Rule Purpose: This rule forwards banking and wire transfer info to the attacker’s e-mail address. It also includes several exclusions to filter out noise that the attacker may not be interested in.
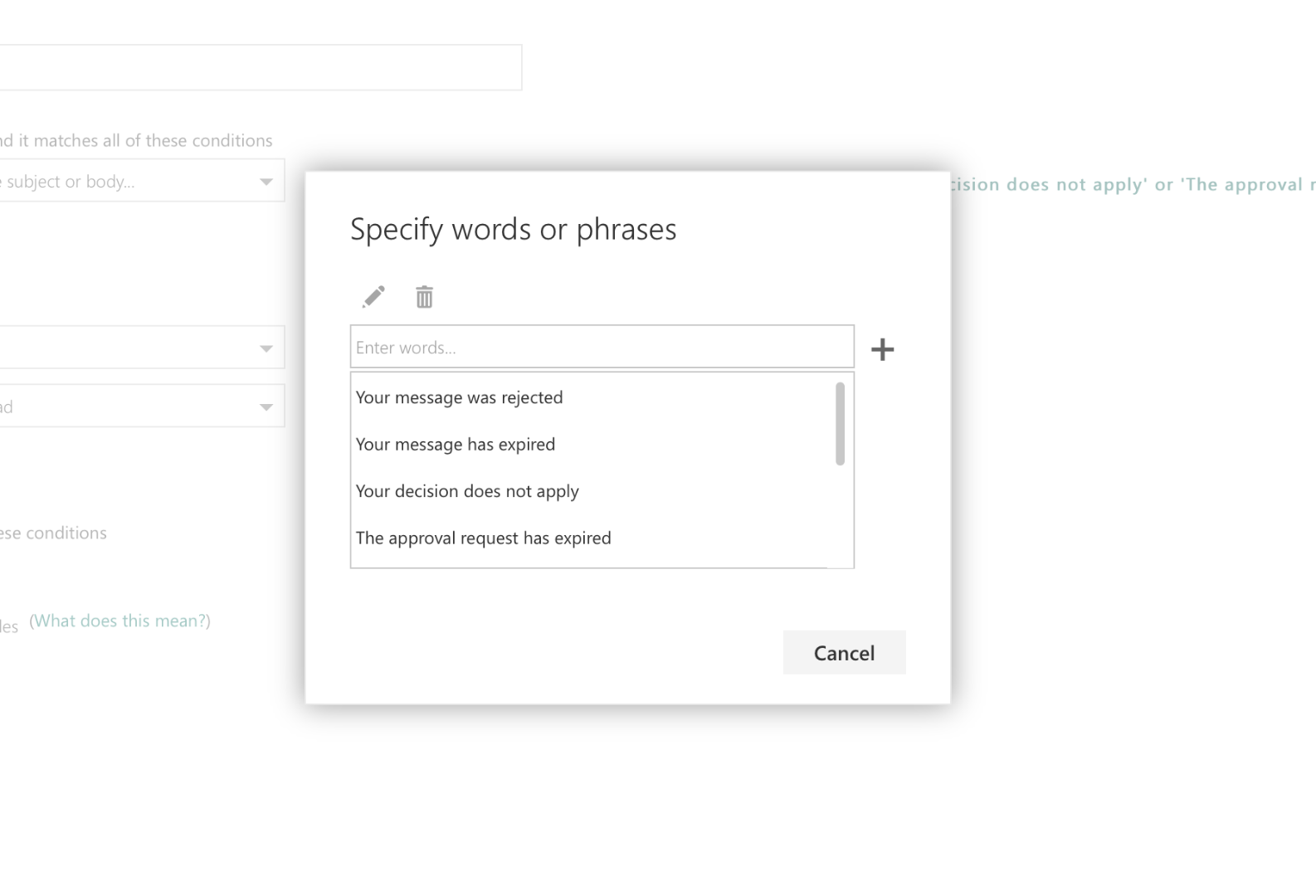
Rule Name: Junk Emails Delete
Rule Function: Look for any emails containing keywords regarding message or request expiration, as well as mandatory service communications and more, marking the e-mail as read and deleting it if matched.
Rule Purpose: This rule is used by the attacker as a way of automatically removing certain e-mails which could let the account owner know the e-mail address is compromised.
Network Indicators
Through the use of passive DNS research, enumeration of domains hosted on the same IP addresses, and analysis of other domains registered with the e-mail address [email protected], Volexity was able to obtain additional indicators that are highly likely associated with the attacker. In some instances, Volexity observed these domains being used in follow-up phishing e-mails. A full list of indicators associated with the campaign are below.
| Domain | IP Address | Notes |
|---|---|---|
| msmfaonline[.]com | N/A | Attacker controlled Microsoft Office 365 themed phishing domain |
| portal.email.msmfaonline[.]com | 137.135.72.110 | FQDN used in Office 365 phishing e-mails. |
| msclickemail[.]com | N/A | Domain included in an Office 365 phishing email, redirecting to the phishing page. |
| portal.login.msclickemail[.]com | 137.135.72.110 | FQDN used in Office 365 phishing e-mails. |
| micorstfonline[.]com | N/A | Domain included in an Office 365 phishing email, redirecting to the phishing page. |
| click.email.micorstfonline[.]com | 137.135.72.110 | FQDN used in Office 365 phishing e-mails. |
| microsftnonline[.]com | N/A | Attacker controlled Microsoft Office 365 themed phishing domain |
| portal.microsftnonline[.]com | 118.27.81.96 | FQDN used in Office 365 phishing e-mails. |
| micrsoftnonline[.]com | N/A | Attacker controlled Microsoft Office 365 themed phishing domain |
| click.email.micrsoftnonline[.]com | 118.27.79.194 | FQDN used in Office 365 phishing e-mails. |
| microsorftnonline[.]com | N/A | Attacker controlled Microsoft Office 365 themed phishing domain |
| micorosorftonline[.]com | 153.122.13.209 | Attacker controlled Microsoft Office 365 themed phishing domain |
| microsofrtfonline[.]com | 211.125.90.191 | Attacker controlled Microsoft Office 365 themed phishing domain |
| microstroftonline[.]com | 157.7.165.120 | Attacker controlled Microsoft Office 365 themed phishing domain |
| microsftsoftonline[.]com | N/A | Attacker controlled Microsoft Office 365 themed phishing domain |
| portal.microsftsoftonline[.]com | 118.27.81.96 | FQDN used in Office 365 phishing e-mails. |
| microstfonline[.]com | N/A | Attacker controlled Microsoft Office 365 themed phishing domain |
| micromsoftonline[.]com | N/A | Attacker controlled Microsoft Office 365 themed phishing domain |
| sieimens[.]com | 192.64.119.79 | Suspect domain found in the e-mail address [email protected] used to register several of the Office 365 phishing domains. |
| msnetcorp[.]com | 103.224.212.249 | Suspect domain being used as a name server for several of Office 365 phishing domains. This domain has a wildcard *.msnetcorp[.]com resoltion to this IP that is used for nameserver, such as ns23.msnetcorp[.]com. |
| mstsnet[.]com | 103.224.212.246 | Suspect domain being used as a name server for several of Office 365 phishing domains. This domain has a wildcard *.mstsnet[.]com resoltion to this IP that is used for nameserver, such as mts63.mstsnet[.]com. |
Conclusion
Using its unique Office 365 monitoring capabilities available to Network Security Monitoring customers, Volexity was able to quickly identify and respond to accounts compromised as a part of this campaign. With so much communication taking place by way of e-mail, corporate Office 365 accounts are a prime target for attackers. Not only are compromised accounts used to send phishing and spam e-mails, but they are also used to steal sensitive information on the affected business, or in the case of this attack, quietly add rules to steal e-mails containing banking or wire transfer information. Enabling two-factor authentication is an excellent way to mitigate many of the risks associated with this attack vector. While not seen on a regular basis, methods for bypassing two-factor authentication do exist, demonstrating the importance of using a security provider with the ability to monitor your Office 365 instance for nefarious activity in the event a breach occurs.