Active Exploitation
Volexity has observed attackers actively exploiting CVE-2019-11510 against vulnerable Pulse Secure VPN servers. Decrypted TLS sessions and logs confirm that attackers have been accessing various files to assist in compromising target networks.
The following files have been observed as part of testing/vulnerability confirmation:
/etc/passwd (testing/confirmation of vulnerability)
/etc/hosts (testing/confirmation of vulnerability)
The following files have been observed being accessed to obtain session IDs, cleartext credentials, and other stored or cached system and user data:
/data/runtime/mtmp/lmdb/randomVal/data.mdb
/data/runtime/mtmp/lmdb/dataa/data.mdb
/data/runtime/mtmp/system
Once the attackers obtained the database files, Volexity observed the following behavior:
- Connections to the VPN using obtained session IDs in order to resume or takeover an existing valid session
- Locally stored accounts cracked and leveraged to connect to VPN services
- Connections to the VPN’s administrative interface using obtained sessions IDs, possibly in an attempt to conduct remote code execution against newly connecting VPN clients
- Login attempts against other corporate resources, such as e-mail, using credentials that were stored by the Pulse Secure VPN server database in the clear
While it should not be a surprise, it should be noted that 2FA will not prevent an attacker from hijacking a valid authenticated session. Once the initial login occurs from the valid user that supplied credentials and a valid second authentication factor, that session can now be hijacked by an attacker who will ride in on the session without further impediment (more on this below).
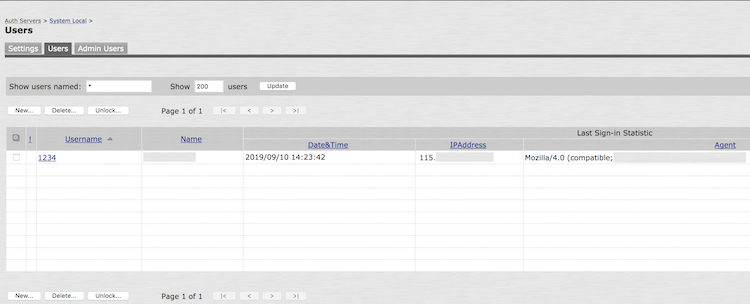
Local Accounts
It is common for an organization to use a separate directory for its users, such as an LDAP server, for authentication. However, Pulse Secure devices will have one or more local administrator accounts. Any of the administrator accounts on the system, such as the default “admin” account, should have their password changed. It should be considered compromised and potentially cracked by a remote attacker. Furthermore, organizations should also check to see if they have any active or valid local accounts that are not administrative users and may potentially have VPN access. These accounts could potentially be set up in a manner that also circumvents 2FA.