Threat Intelligence
Go Get ‘Em: Updates to Volexity Golang Tooling
August 11, 2025
This blog post was the final deliverable for a summer internship project, which was completed under the direction of the Volexity Threat Intelligence team.
If you’d like more information about internships at Volexity, please contact us!
As noted in Volexity’s April 2025 blog post, Golang continues to grow in popularity across the developer community, including developers of malicious software. Furthermore, a significant portion of samples encountered by Volexity have been obfuscated by Garble or other such tools.
Volexity’s GoResolver tool was released to help with analysis of these samples, reducing analyst load when working with obfuscated Golang binaries. However, there are still some difficulties when working with Golang samples, even in the absence of obfuscation. Challenges include organization of string information and propagation of runtime type information.
To ease these challenges Volexity has released a new utility, GoStringExtractor, and added functionality to the existing GoResolver tool.
Introducing GoStringExtractor
Volexity’s GoStringExtractor is a plugin utility available for IDA Pro and Ghidra that helps search and analyze string data in a Go binary, provided they have not been destroyed by an obfuscation tool, such as Garble’s -literals flag.
Inspecting string data often provides insights into program behavior. Analysis of available strings is useful not only for reverse engineering and binary analysis, but also detection engineering. Unfortunately, the way the Go compiler organizes string data complicates analysis for several reasons:
- All strings are stored in a contiguous table and not individually terminated.
- The location and size of the string table is not recorded in runtime structures.
- Strings for all linked Go packages are included in the string table.
Fortunately, the organization of the string table is consistent across different operating systems and architectures. Although the strings are unterminated, they are ordered first by length and then alphabetically. As such, once an entry in the table is identified, walking the table is relatively simple using the cross-referencing features of the Software Reverse Engineering (SRE) platform.
GoStringExtractor creates a JSON report of all referenced strings and the names of their referencing functions. Further, the plugin provides an option to define the strings neatly inside your IDA Pro or Ghidra database. A before-and-after comparison is shown in Figures 1 & 2 below.
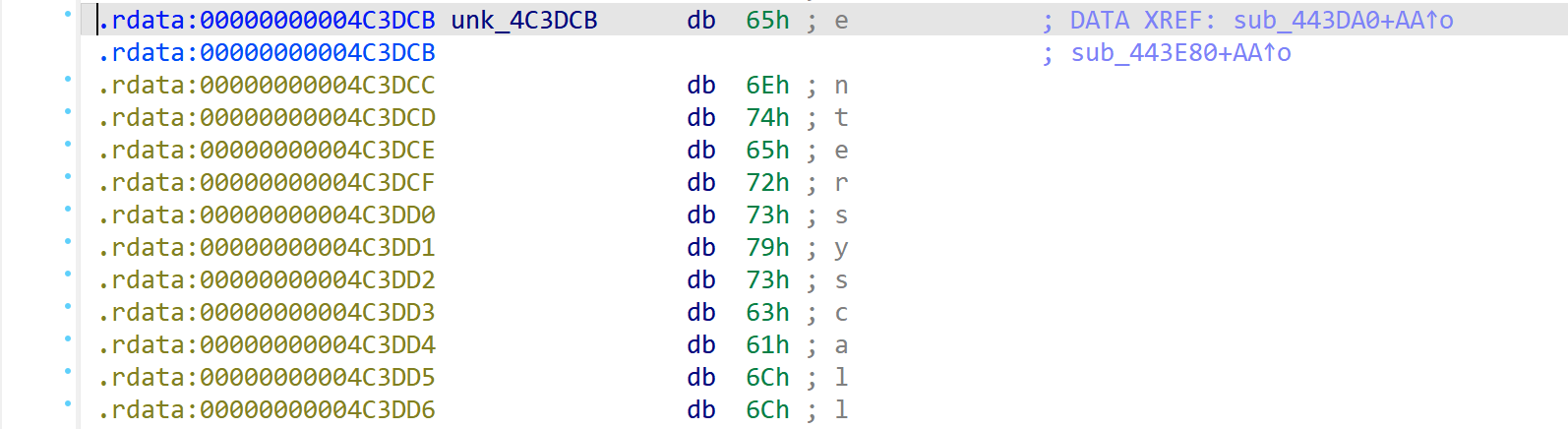
Figure 1. An entry in the string table prior to running GoStringExtractor
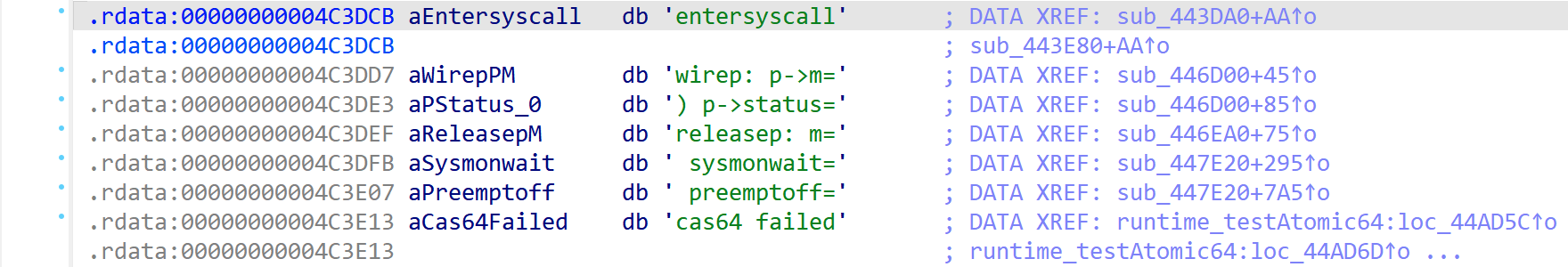
Figure 2. String table following GoStringExtractor analysis
GoStringExtractor also provides a feature to filter the string report based on the package name referencing the string. This is useful when you want to focus on strings present in attacker code, rather than library code.
Type Parsing Added to GoResolver
Features of the Golang runtime environment, such as garbage collection, rely on high-level type information built into a binary at compile time. This information is collectively referred to as runtime type information (RTTI). Especially in binaries linking many packages, access to a program’s RTTI provides significant insight into a binary’s organization and capabilities. When a binary is obfuscated, the build information is stripped, and many SRE tools will not attempt to recover any of this type information. Even when a binary is not obfuscated, SRE tools can sometimes be unreliable in recovering RTTI.
Figures 3 & 4 below show what an analyst may encounter if the RTTI of a sample is not correctly parsed.
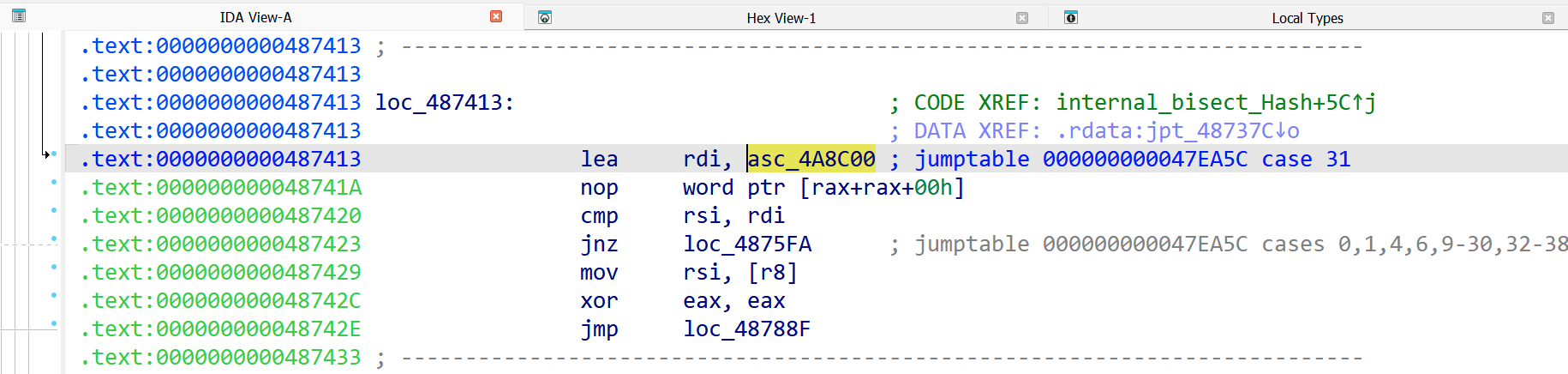
Figure 3. An arbitrary address is being loaded into the rdi register
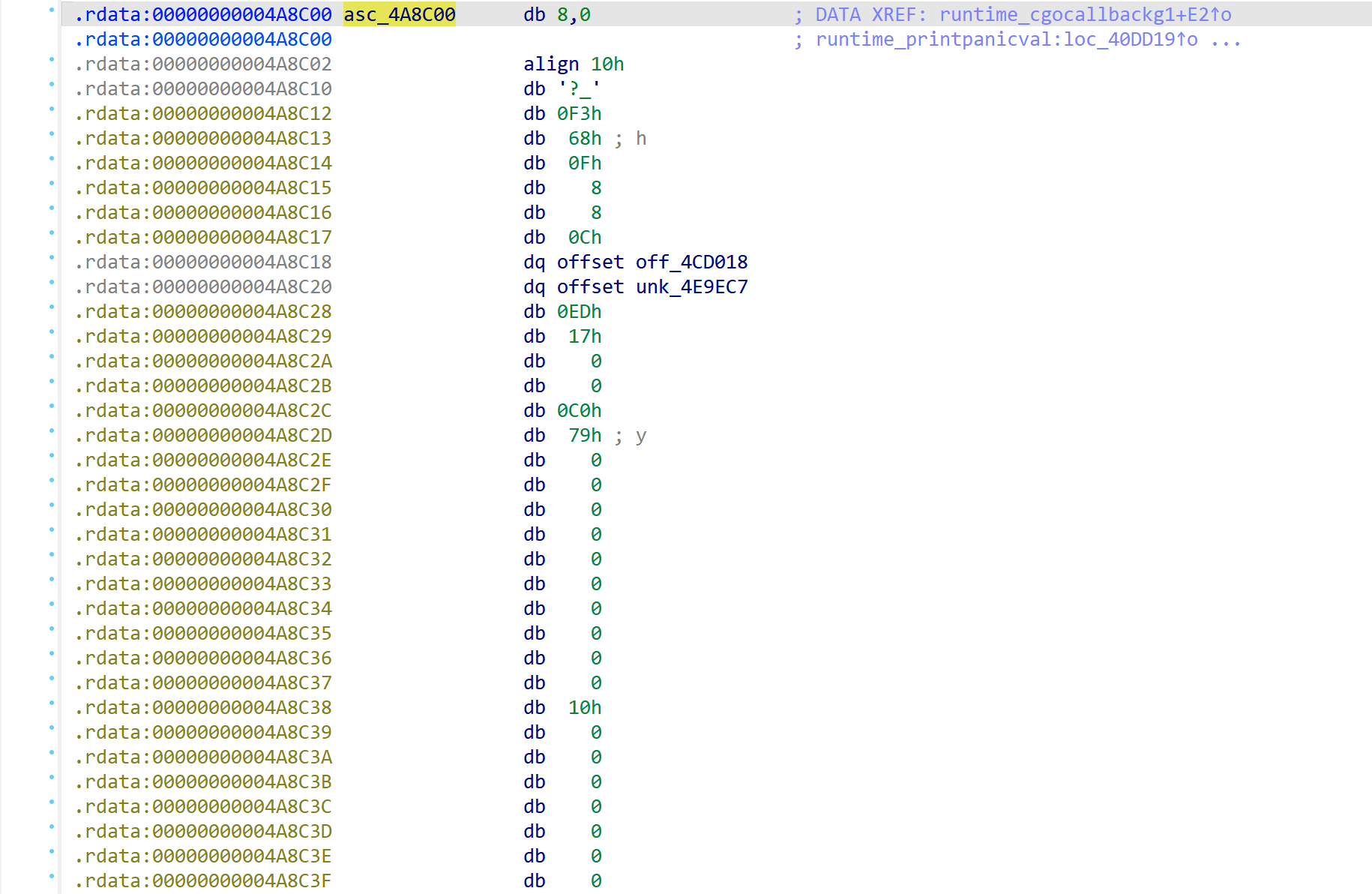
Figure 4. Unprocessed data at address 0x4a8c00
In Figure 3 an arbitrary address is loaded into a register before a comparison operation. Following the address to the loaded data, as shown in Figure 4, shows a large block of unorganized data. This isn’t particularly useful during analysis. However, once RTTI is correctly applied by GoResolver, the disassembly output is changed, as shown in Figures 5 & 6.
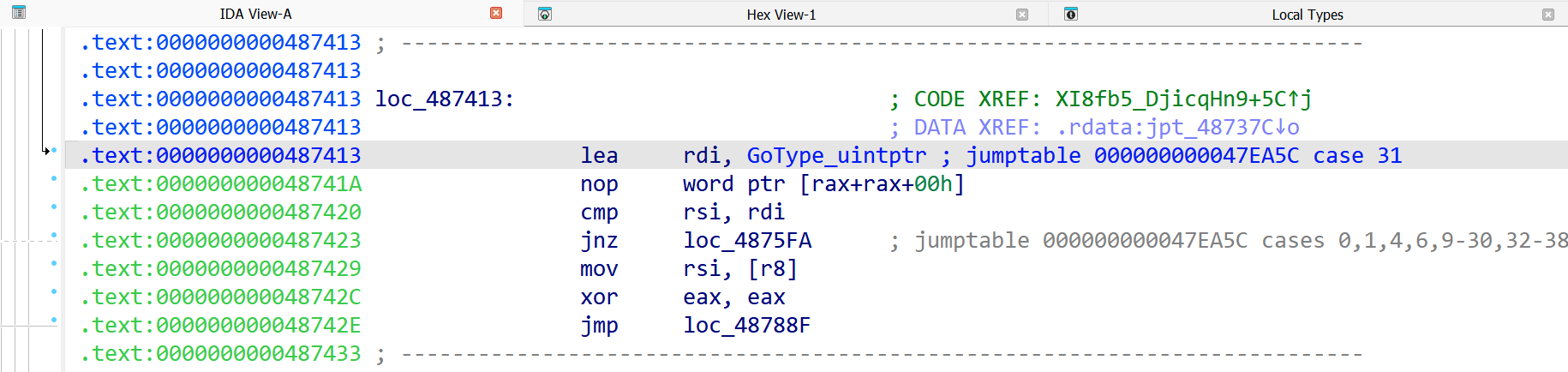
Figure 5. Corrected type-reference applied by GoResolver
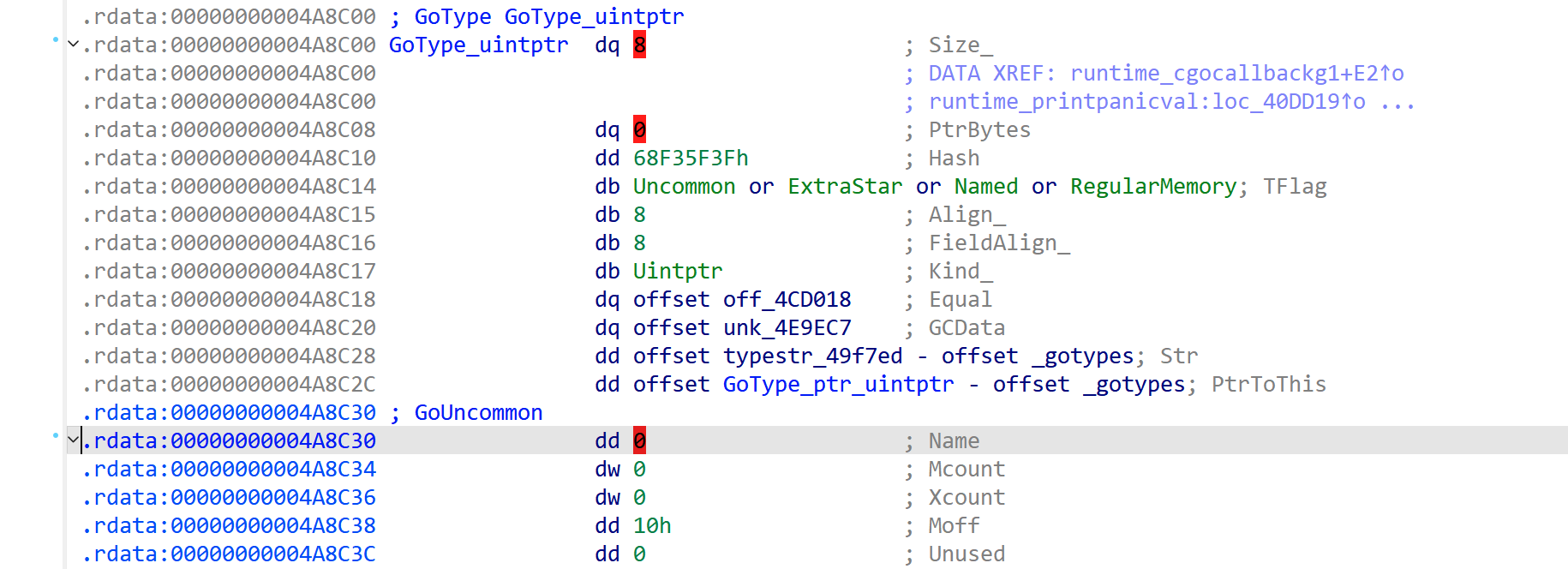
Figure 6. The data for the type is now organized and clear
To include type parsing into the GoResolver workflow, simply pass the new -y flag into the command to extract all runtime types, like so:
goresolver -y -x sample_bin.exe
This will add two new members to the JSON report: the types address, followed by every type found in the binary. If you choose not to include type data on the command line, these members will have null values. Figure 7 below is an example of the updated JSON report format.
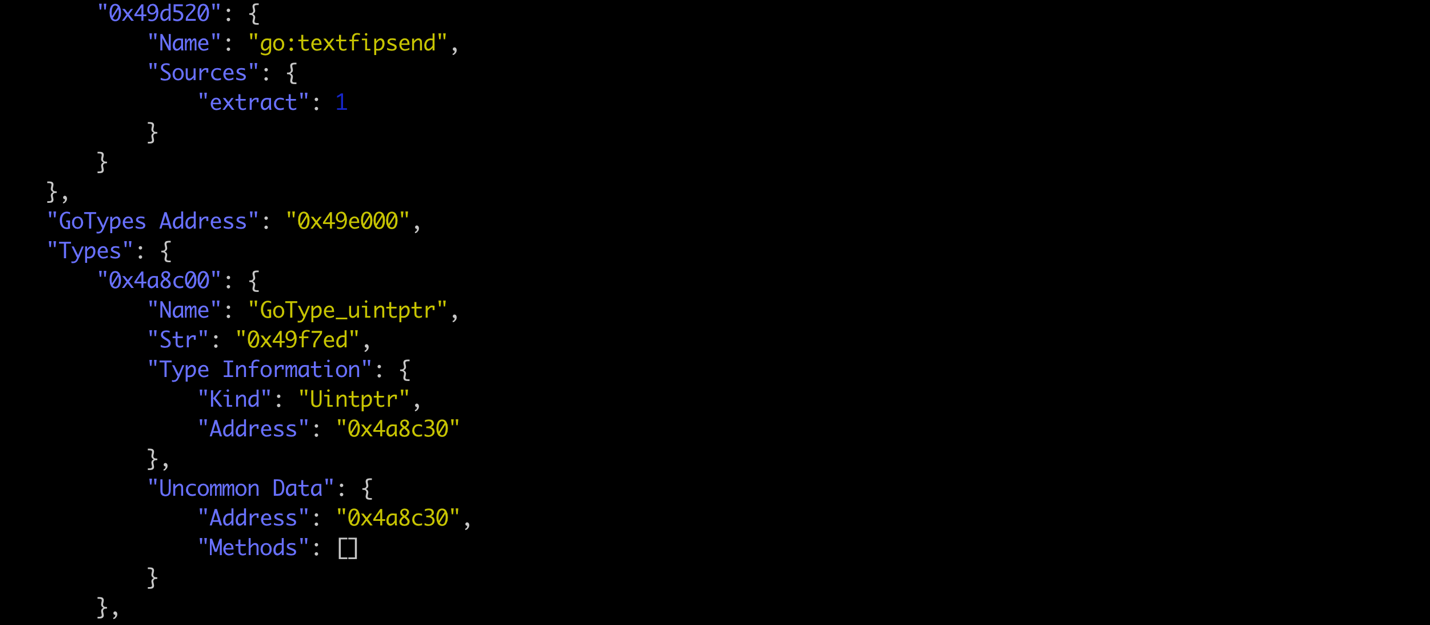
Figure 7. JSON output of GoResolvers RTTI parsing
With the newly added RTTI parsing feature, Volexity also made updates to the IDA Pro and Ghidra plugins to make the import of the JSON file compatible with the new type information. When the JSON report is imported into the SRE tool, it will define each of the types in the database as shown below in Figures 8 & 9.
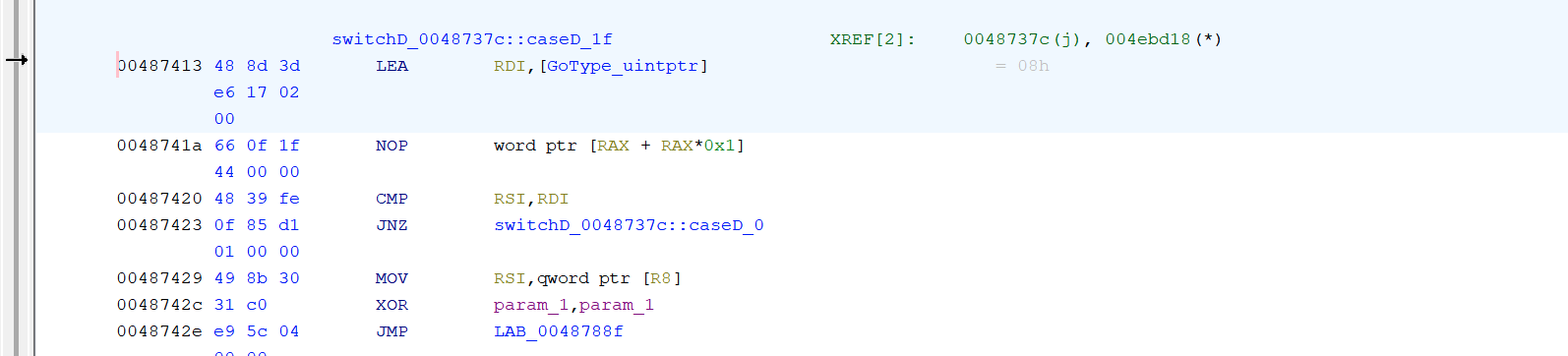
Figure 8. Ghidra disassembly view after types are imported with GoResolver
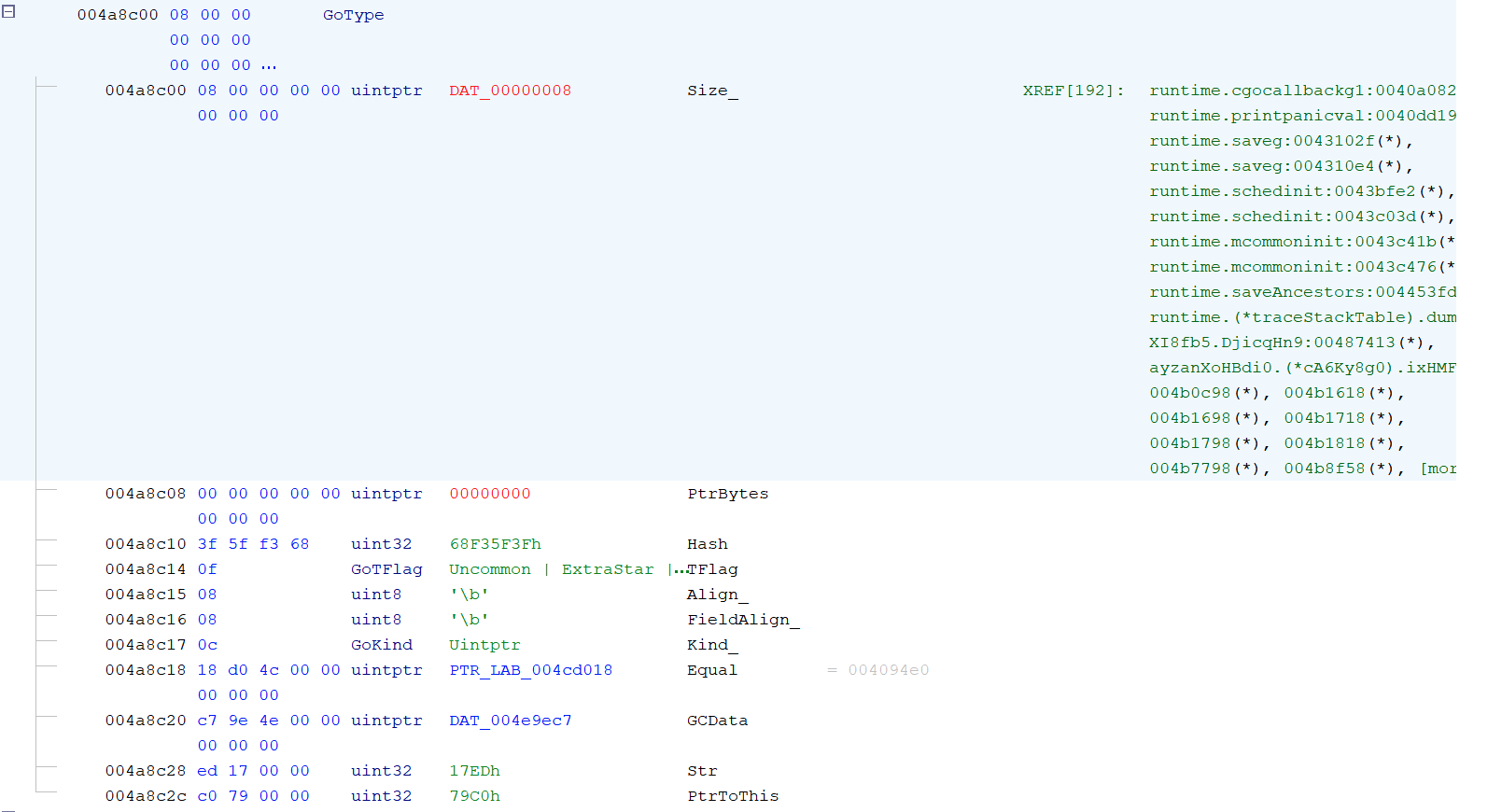
Figure 9. A RTTI entry created by GoResolver in Ghidra
GoResolver’s RTTI parsing works across all operating systems, as well as 32- or 64-bit architecture samples.
KEY TAKEAWAYS
- Volexity is releasing a new tool, GoStringExtractor, a tool to aid in parsing string data from Golang binaries.
- Parsing of runtime type information has been added to GoResolver.
- Helper tools GoStrap and GitToolFetcher have been parallelized to improve performance.
Try It Out!
Download and use the newly updated features in GoResolver and the new GoStringExtractor plugin utility discussed in this blog post.