
Threat Intelligence
Dangerous Invitations: Russian Threat Actor Spoofs European Security Events in Targeted Phishing Attacks
December 4, 2025
In early 2025, Volexity published two blog posts detailing a new trend among Russian threat actors targeting organizations through the abuse of Microsoft 365 OAuth and Device Code authentication workflows to gain access to Microsoft user accounts. Despite detailing these activities publicly, Volexity continues to see similar techniques being leveraged by Russian threat actors to heavily target both Microsoft and Google environments. While the techniques are similar, what changes is the variety of methods & themes used to target and socially engineer users.
In this blog post, Volexity explores two new campaigns observed abusing the OAuth and Device Code authentication workflows to phish credentials from end users. These attacks involved the creation of fake websites masquerading as legitimate international security events taking place in Europe, with the aim of tricking users who registered for these events into granting unauthorized access to their accounts. The following real events were used for this purpose in the campaigns observed by Volexity:
- Belgrade Security Conference (November 17-19, 2025)
- Brussels Indo-Pacific Dialogue (December 2, 2025)
These campaigns used various methods to ensure success, including the following:
- Rapport-building phishing: The attacker often establishes communications with victims. No malicious content is shared, at first. Only later is a phishing link sent, once the targeted user has confirmed their interest.
- Fake websites: The attacker creates dedicated, polished, and professional-looking websites to help facilitate attacks.
- Guiding users via WhatsApp/Signal: The attacker offers to provide “live support” to targeted users via messaging apps to ensure they correctly return the URL, in the case of OAuth phishing workflows.
Volexity attributes these new campaigns to the Russian threat actor it tracks as UTA0355. This is the same threat actor previously reported on in April 2025 by Volexity.
Belgrade Security Conference
In October 2025, Volexity worked an incident where a user’s Microsoft 365 account had been identified as compromised following the detection of anomalous login activity. An investigation into the incident found the user had received a spear-phishing email leading to an OAuth authentication workflow. The email had come from an account the user had recently corresponded with, and it was a continuation of an existing and legitimate thread related to the upcoming Belgrade Security Conference in Serbia. This method of phishing would further require the targeted user to send to the attacker a code generated by Microsoft that would be found in the URL bar of the user’s browser. There was no email correspondence indicating what to do with this code, so Volexity suspected the attacker was communicating with the victim outside of email.
Working with its customer, Volexity found the threat actor had been actively communicating with this targeted user on WhatsApp. The attacker had reached out under two different identities related to the Belgrade Security Conference, both of which had been compromised. The first identity used on WhatsApp simply reached out to inform the user that their “colleague” would be contacting them shortly. The second WhatsApp identity then purported to be from that colleague, who was an individual in the email thread, and primed them for an invitation email.
The attacker then engaged the user using rapport-building phishing, first engaging them in a benign conversation, and later sending an invite to register for resources tied to the Belgrade Security Conference, as shown below:
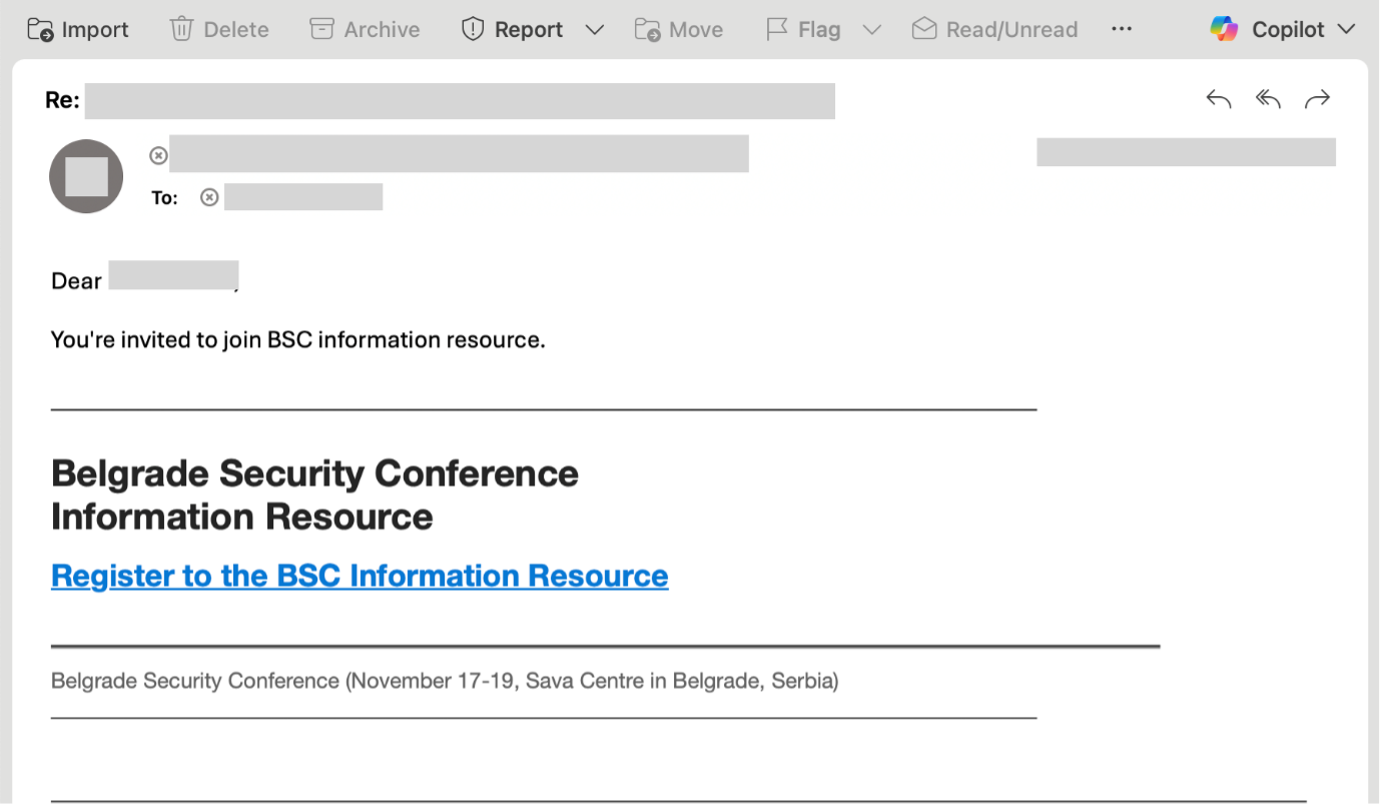
The hyperlink in the email above led to a Microsoft-owned URL that could be abused as part of an OAuth phishing workflow:
https://login.microsoft[.]com/common/oauth2/authorize?client_id=29d9ed98-a469-4536-ade2-f981bc1d605e&resource=01cb2876-7ebd-4aa4-9cc9-d28bd4d359a9&redirect_uri=https%3A%2F%2Flogin.microsoftonline.com%2FWebApp%2FCloudDomainJoin%2F8&response_type=code&amr_values=ngcmfa&login_hint=[user]
After the targeted user completed the login, they landed on a blank webpage whose URL contained the OAuth token. The attacker asked the user to provide the URL under the guise of “finalizing their registration” to complete the process.
After successfully phishing the user, the attacker used the user’s Microsoft account to access a wide variety of files through Microsoft 365. Some noteworthy features of this access include the following:
- A device named DESKTOP-[REDACTED] was used to access data.
- A new device was created in Microsoft Entra ID to maintain access to the account. The device was given the same name as an existing device belonging to the user. For example, if the user’s device was named was “Charles E. Cheese’s iPhone”, the newly registered device would be given the same name.
- The user agent for requests was Dalvik/2.1.0 (Linux; U; Android 14; 2211133C Build/UKQ1.230705.002) ;Xiaomi.
In this specific case, it was notable that the “iPhone” access was coming from a device claiming to be an Android phone.
Phishing Operations Expanded
Not long after this highly targeted operation, Volexity observed broader targeting from an attacker-created Gmail account. In November 2025, Volexity observed this Gmail account sending several spear-phishing messages to a variety of targets across Volexity’s customer base. All the phishing messages linked to a newly created website, bsc2025[.]org, that masqueraded as a dedicated domain for the Belgrade Security Conference. The decoy page is shown below.
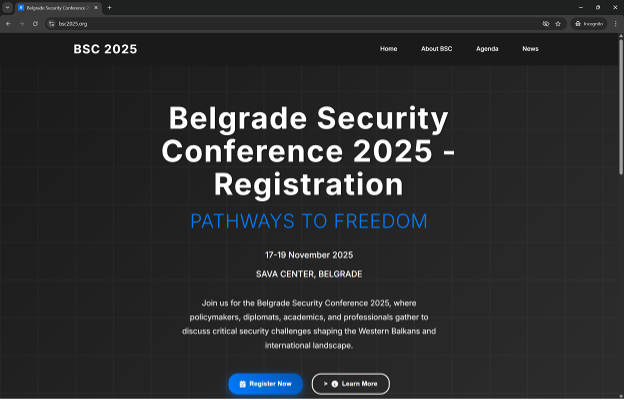
In the phishing email, users were encouraged to use this webpage to register for the event. When registering, users are prompted that a “Corporate Email” is required, as opposed to a “personal email”, as shown below.
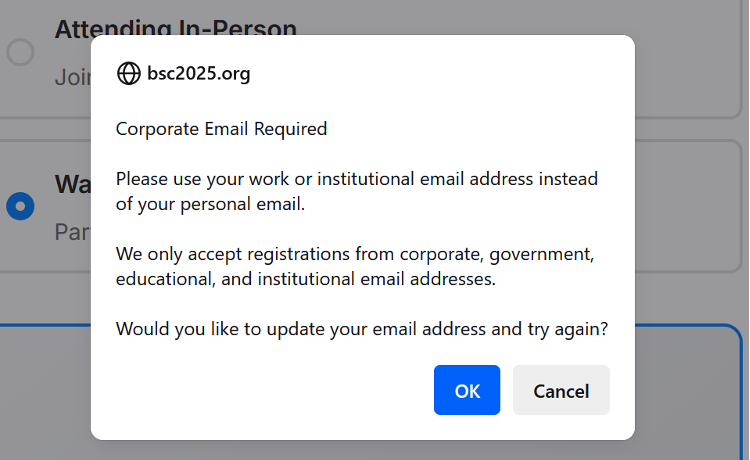
Registering for the event via bsc2025[.]org using a corporate (enterprise) account would lead to one of two workflows:
- If the provided email domain was not of interest to the attacker, the attacker would set a cookie named cookie_reg containing a Base64-encoded version of the registrant email. The user would then be redirected to a page indicating they were registered for the conference along with their “registration” details.
- If the provided email domain was of interest to the attacker, the same cookie_reg cookie would get set and the registration information for the user recorded. However, the user would then be redirected to a Microsoft 365 phishing workflow, where the user is asked to sign in via a URL with the following format:
https://login.microsoftonline[.]com/common/reprocess?ctx=rQQIARAAJU3P[snipped]m5T2D81&sessionId=941739c9[snipped]2e06bf63f947
To a user, the webpage will look like a real login page for Microsoft 365. The only clue they are being phished is the Microsoft Authentication Broker dialogue shown below, which occurs after authentication with Microsoft services has been completed.
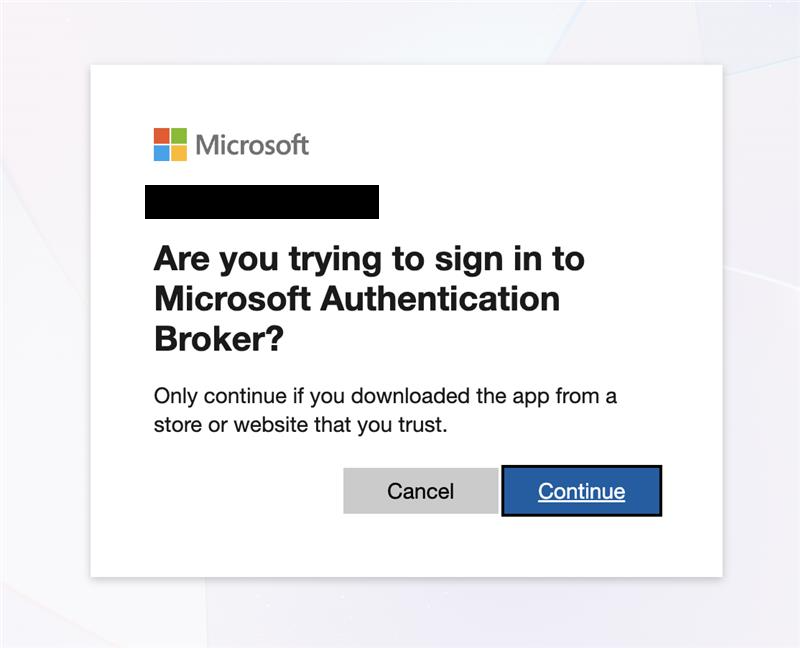
Volexity notes that Microsoft Authentication Broker is the same application configured by default in the DeviceCodePhishing project available on Github. When Volexity provided the attacker with credentials in this way, via a honeypot account, Volexity observed subsequent attempted attacker activity via a residential Comcast IP address in the United States, which according to spur.us, belonged to a proxy network.
Brussels Indo Pacific Dialogue
Volexity was also tracking a separate campaign also attributed to UTA0355 in the same timeframe. In this second campaign, the emails purported to be from an individual at the Centre for Security, Diplomacy, and Strategy (CSDS) at Vrije Universiteit Brussel in Belgium. The initial observed emails invited recipients to participate in an upcoming event called the Brussels Indo-Pacific Dialogue (BIPD). Volexity detected spear phishing campaigns aimed at its customers, where targeted users were individuals working on foreign policy, matters related to Europe, or who had previously worked in senior positions in the United States government. An example of the initial outreach is shown below.
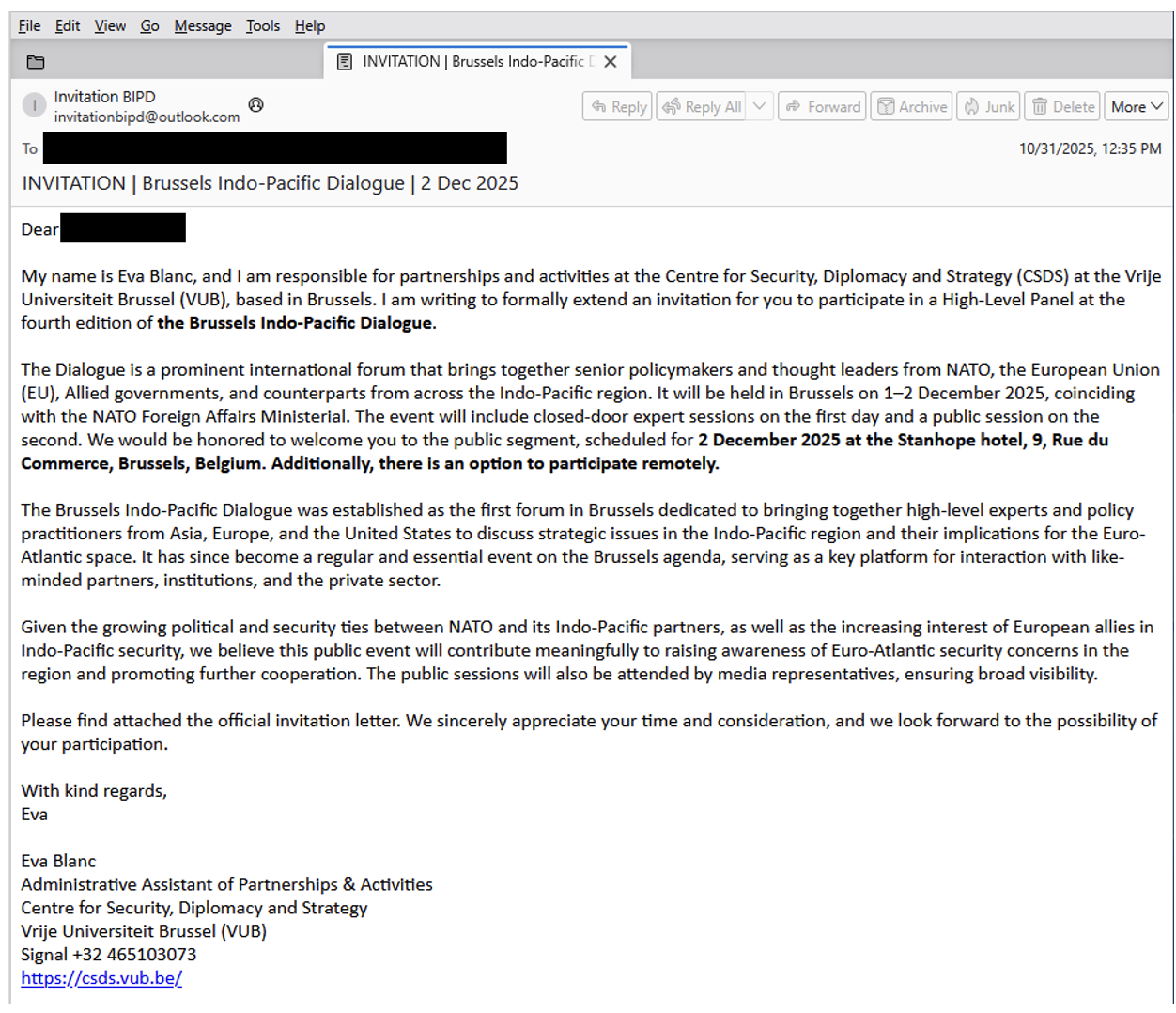
After exchanging a few emails with the targeted user, the sender shared a URL in a follow-up email, noting that the user needed to be added to the “BIPD system” by clicking a malicious URL, as shown below. The URL shared with the user was unique to the targeted user.
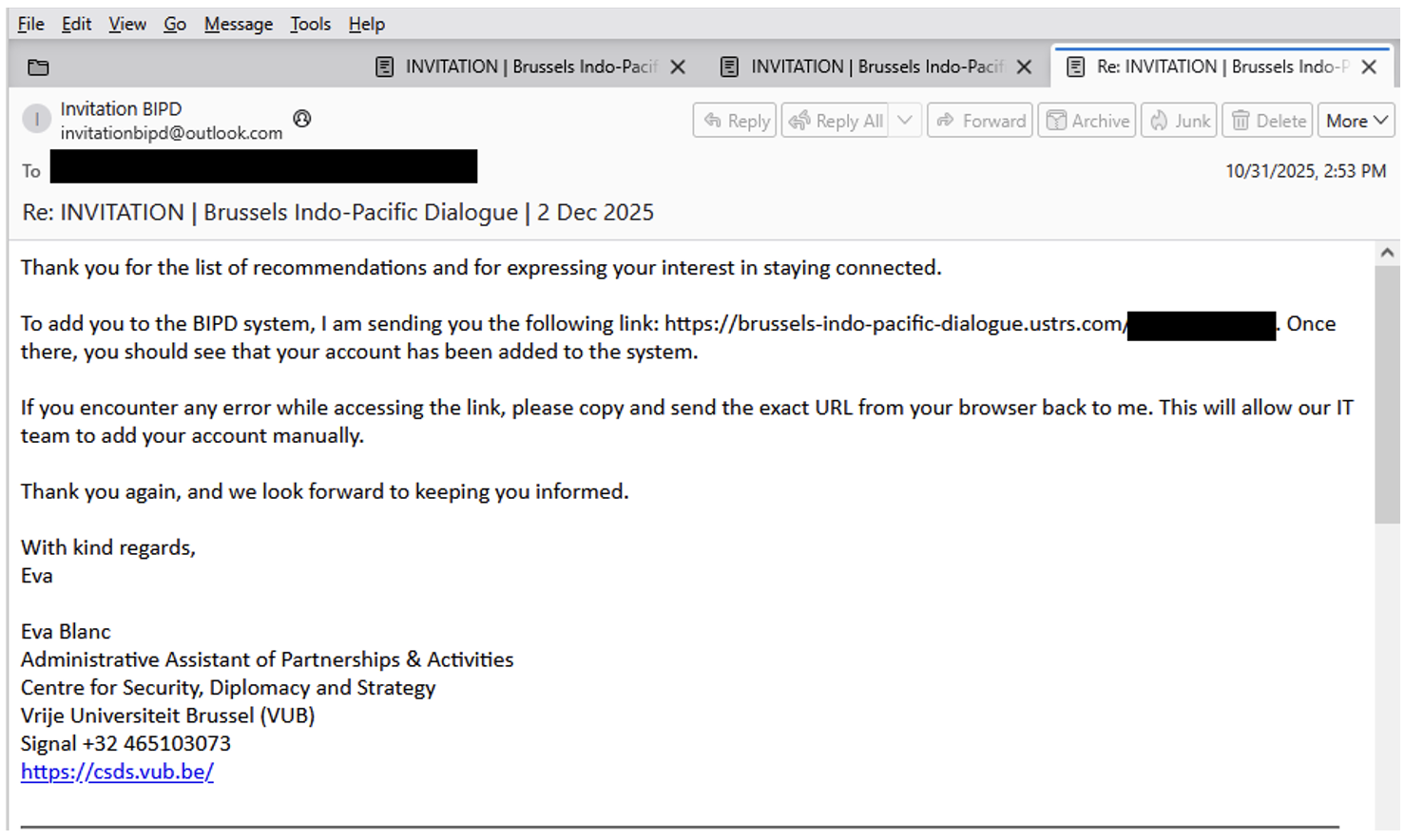
At the time of analysis, the unique URL was not functional; however, in the email, the attacker requests that in the event of an error, the user should “copy and send the exact URL” from the browser, which is consistent with OAuth code phishing techniques.
The domain used, ustrs[.]com, appears to have been purchased using a domain auction service or similar. WHOIS data for the domain shows the original create date of 2020-02-05, but it was updated on 2025-10-31. This is a tactic to defeat reputation-based services that use the age of a domain as a risk indicator. An excerpt from the WHOIS record is given below:
Domain Name: USTRS.COM
Registry Domain ID: 2488656711_DOMAIN_COM-VRSN
Registrar WHOIS Server: whois.dynadot.com
Registrar URL: http://www.dynadot.com
Updated Date: 2025-10-31T14:30:50.0Z
Creation Date: 2020-02-05T03:19:46.0Z
Registrar Registration Expiration Date: 2026-02-05T03:19:46.0Z
In November 2025, Volexity observed the same email sender contacting other Volexity NSM customers, this time sharing a link to the dedicated website brussels-indo-pacific-forum[.]org for users to register for the conference. This website was impersonating the BIPD, as shown below.
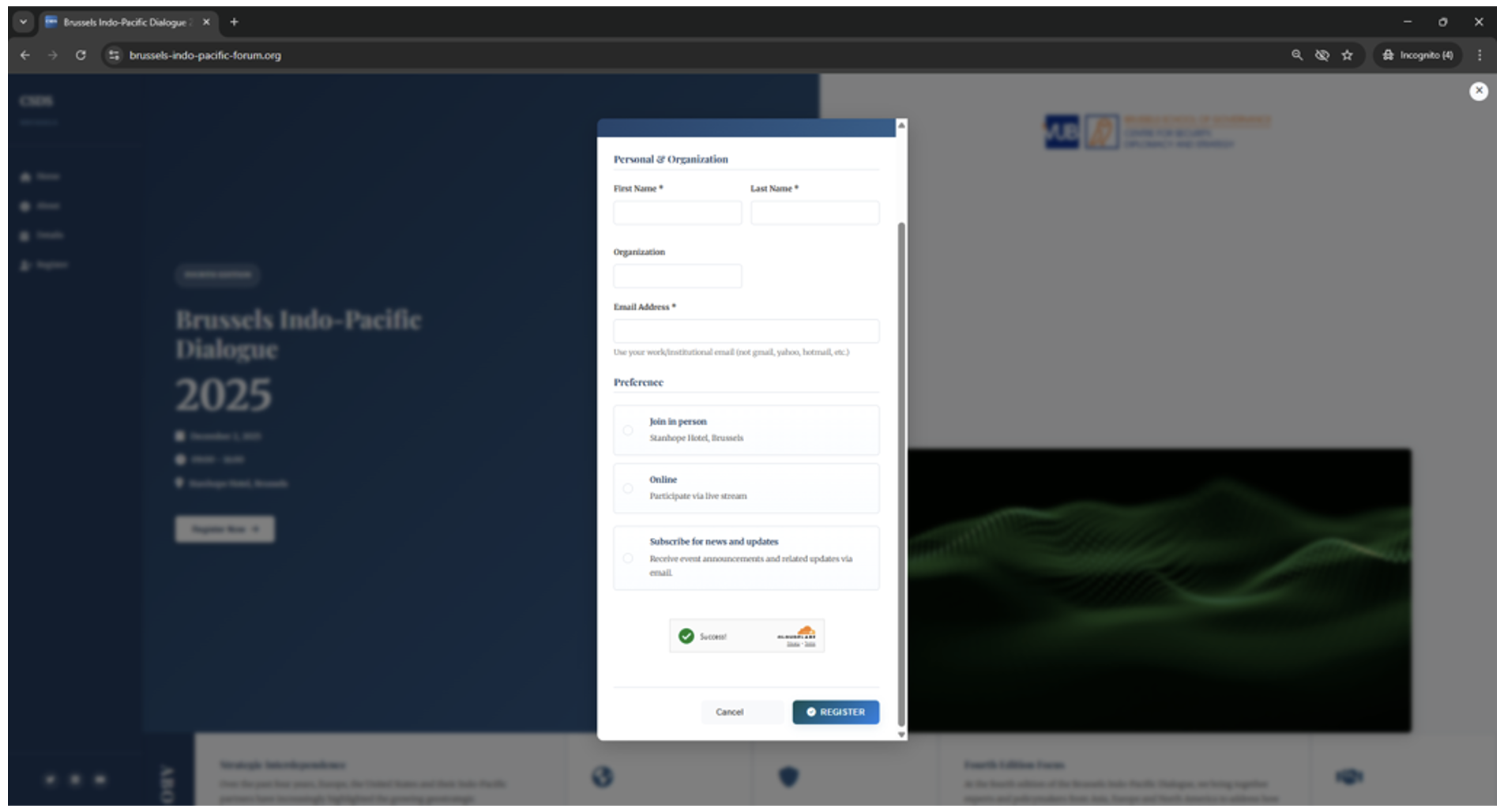
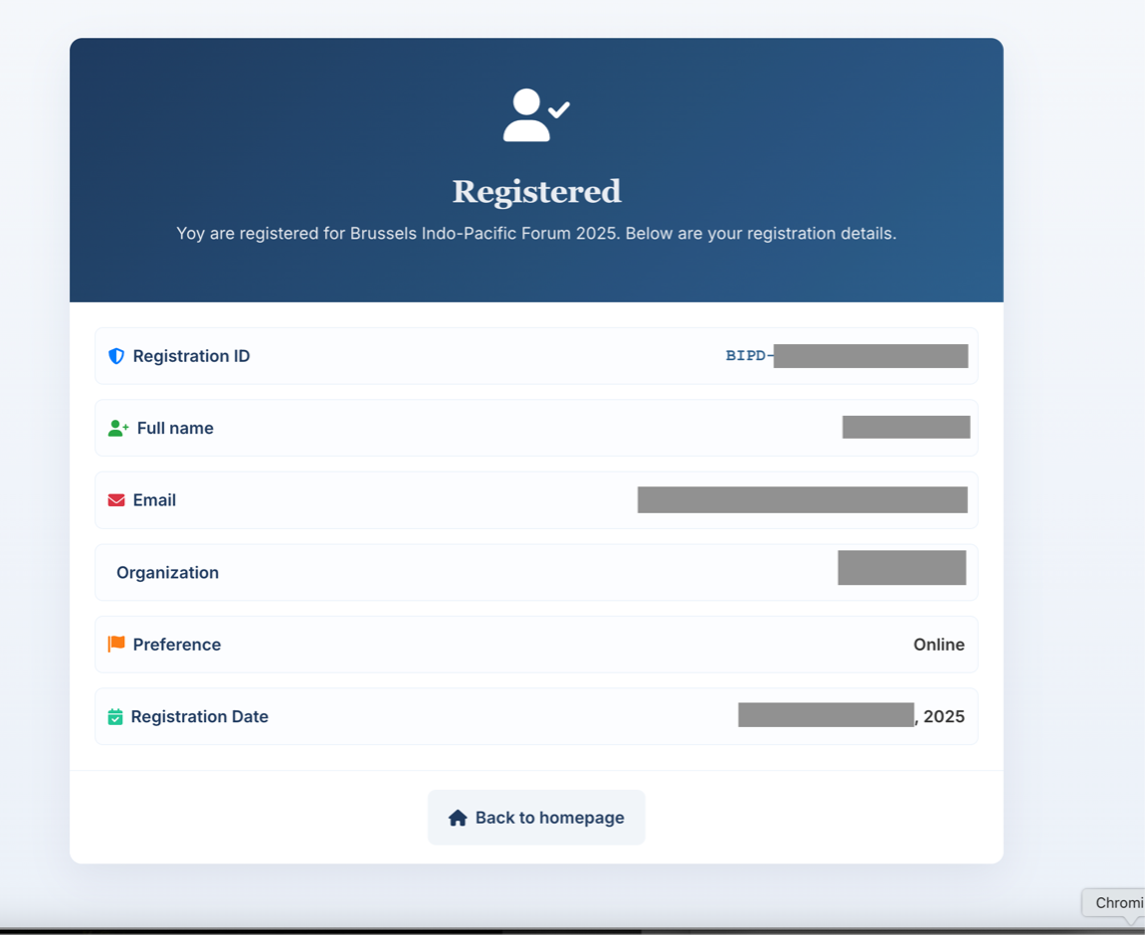
Visiting the website and attempting to register led to an attack path where the target is presented with a Microsoft 365 Device Code phishing workflow masquerading as a legitimate signup process. Once successfully “registered”, non-targeted users will be directed to page with their registration details as shown below.
As was the case in the Belgrade Security Conference campaign, subsequent access to compromised accounts takes place via nodes belonging to proxy networks.
Expanding the Target List
Volexity also observed multiple cases where UTA0355 managed to expand their target list by making requests to those they had originally attempted to spear phish. When a user would reply back to UTA0355’s conference invitation indicating that they were unable to attend or participate in the event, the threat actor would often respond back with two requests. The first request would still invite the initial target to register so that they received future updates. The second request would be to provide the names and email addresses of any other colleagues that might also be interested in the event. Volexity observed multiple cases where additional contacts were provided back to UTA0355. In at least one case Volexity further observed an unwitting individual make an introduction between a new target and UTA0355.
World Nuclear Exhibition
The WHOIS record for the bsc2025[.]org domain, which impersonates the Belgrade Security Conference, showed that the attacker used an email account from the obscure email service mailum[.]com to register the domain, as shown below.
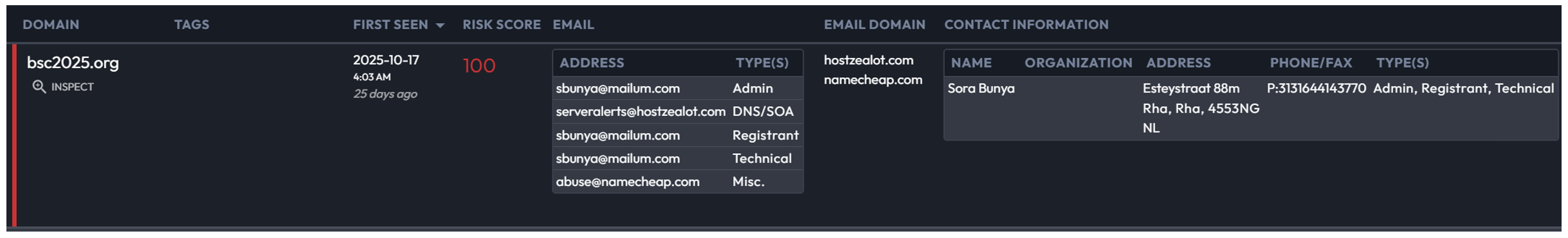
Investigation of other domains registered with email addresses that used the same service yielded additional related infrastructure masquerading as the World Nuclear Exhibition, which place November 4-6, 2025. Through its investigation, Volexity discovered the following domains:
- world-nuclear-exhibition-paris[.]com
- wne-2025[.]com
- confirmyourflight-parisaeroport[.]com
Volexity is unable to confirm the usage of these domains but believes it is possible they may have been employed in earlier attacks by UTA0355.
Conclusion
Since documenting Russian threat actors targeting Microsoft 365 users and organization with Device Code and OAuth workflows earlier this year, Volexity has continued to see a significant increase in these techniques being used in highly targeted attacks. While these workflows have been viable for a long time, it appears various threat actors have increased adoption and reliance on them. Volexity suspects this is due to the level of success threat actors are having at breaching accounts in this manner. The campaigns described in this blog post are just a small subset of observed attacks this year, and based on Volexity’s observations they continue to be quite effective. This is particularly true when combined with clever social-engineering techniques, such as rapport building phishing and the use of fake websites impersonating legitimate websites.
Some factors that stood out to Volexity during these campaigns are summarized below:
- The “registration” workflow for both the BIPD and BSC events is reminiscent of real-world authentication workflows, where users are asked to perform SSO against various services.
- Referencing upcoming events as a pretext to engage users has also proven effective. Volexity has observed users directly forwarding event invitations to other users within their organization who may be suitable attendees. Effectively, users help the attacker build a target list for both that particular phishing campaign and others in the future.
- Using compromised accounts to send phishing content is a risky move for threat actors, as it can potentially reveal their intrusion when users report the phish to the initially compromised organization. On the other hand, the use of compromised accounts for phishing can lend credibility to an attack, which Volexity assesses with medium confidence results in high success rates for click-throughs.
- The continued use of contacting targets via messaging apps such as WhatsApp or Signal ahead of or during the spear-phishing campaign provides an additional point of contact and legitimacy to the operations.
The effort required to create websites that mimic real-world events, impersonate individuals associated with those events, and contact users directly on messaging applications demonstrates that UTA0355 is a well-resourced and capable threat actor.
Indicators associated with these campaigns are available here.
Investigative Assistance
If any organization or individual believes they may have been targeted by UTA0355, or by a similar attack, please feel free to reach out to Volexity via our contact form. We would be glad to assess any potential targeting and assist in determining if such an attack may have succeeded.
Volexity’s Threat Intelligence research, such as the content from this blog, is published to customers via its Threat Intelligence Service. The activity described in this blog post was shared with Volexity Threat Intelligence customers in TIB-20251117 & TIB-20251119B.
If you are interested in learning more about Volexity’s services, including Network Security Monitoring & Incident Response, or our leading memory forensics solutions, Volexity Surge Collect Pro for memory acquisition and Volexity Volcano for memory analysis, please do not hesitate to contact us.
Acknowledgements
Volexity would like to thank its customers for their vigilance, cooperation, hard work, and dedication to defending human rights.
KEY TAKEAWAYS
- Fake malicious websites impersonated legitimate European conferences in highly targeted credential-stealing operations.
- Compromised accounts and spoofed identities were used to invite and lure users.
- Microsoft Device Code and OAuth workflows were abused to gain access to account.