Threat Intelligence
Phishing for Codes: Russian Threat Actors Target Microsoft 365 OAuth WorkflowsApril 22, 2025

Threat Intelligence
Phishing for Codes: Russian Threat Actors Target Microsoft 365 OAuth WorkflowsApril 22, 2025

Threat Intelligence
GoResolver: Using Control-flow Graph Similarity to Deobfuscate Golang Binaries, AutomaticallyApril 1, 2025

Threat Intelligence
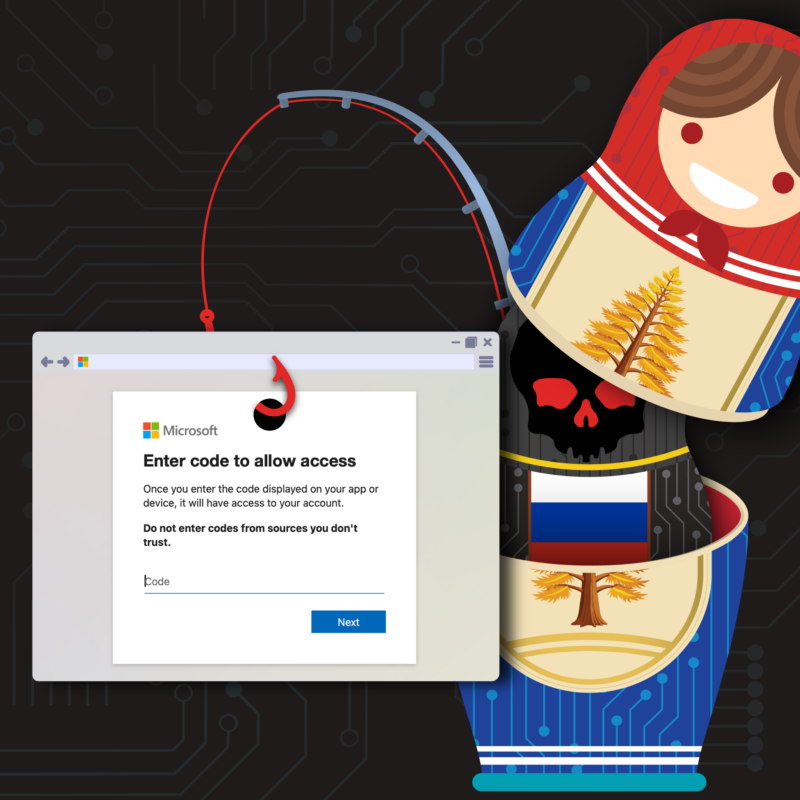
Multiple Russian Threat Actors Targeting Microsoft Device Code AuthenticationFebruary 13, 2025
Threat Intelligence
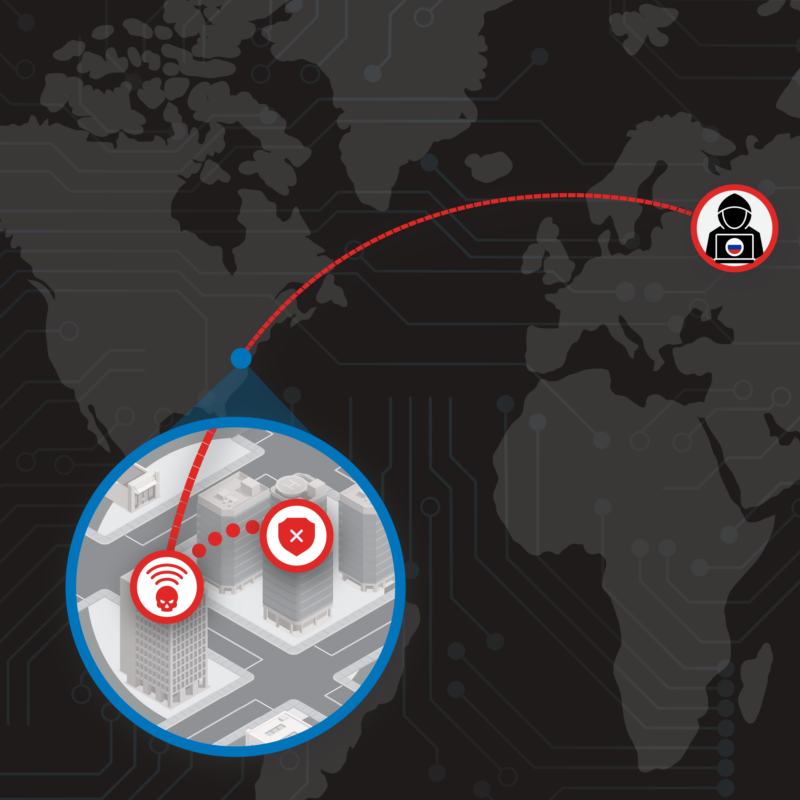
The Nearest Neighbor Attack: How A Russian APT Weaponized Nearby Wi-Fi Networks for Covert AccessNovember 22, 2024
Threat Intelligence
BrazenBamboo Weaponizes FortiClient Vulnerability to Steal VPN Credentials via DEEPDATANovember 15, 2024

Threat Intelligence
StormBamboo Compromises ISP to Abuse Insecure Software Update MechanismsAugust 2, 2024

Threat Intelligence
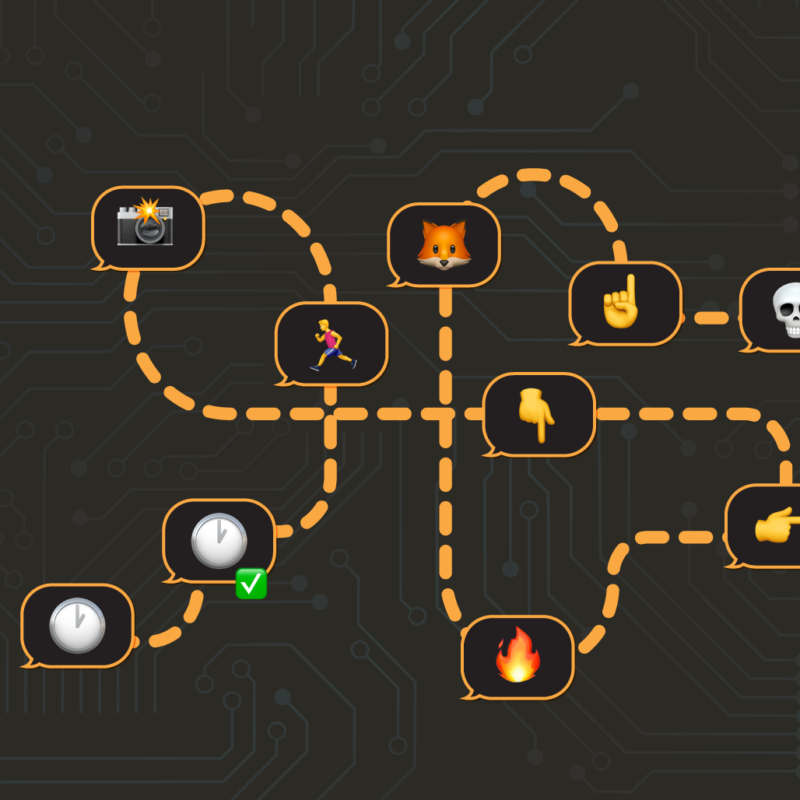
DISGOMOJI Malware Used to Target Indian GovernmentJune 13, 2024
Memory Forensics
Detecting Compromise of CVE-2024-3400 on Palo Alto Networks GlobalProtect DevicesMay 15, 2024